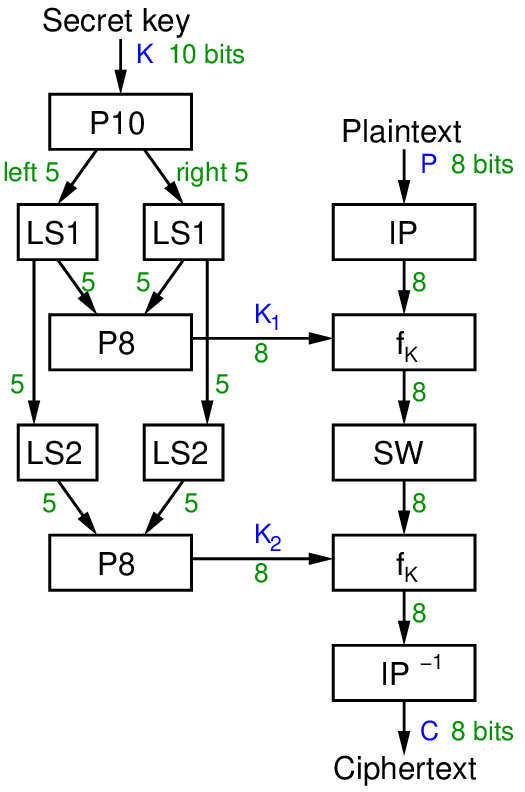
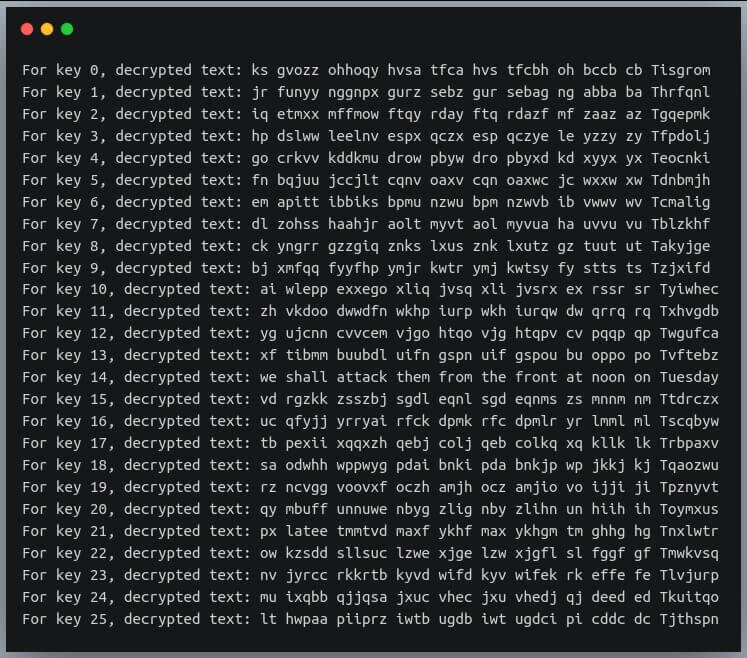
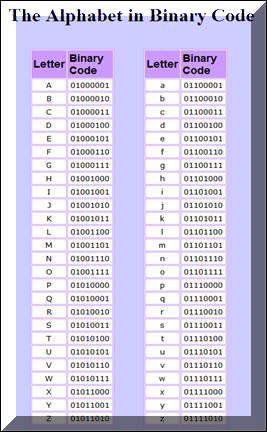
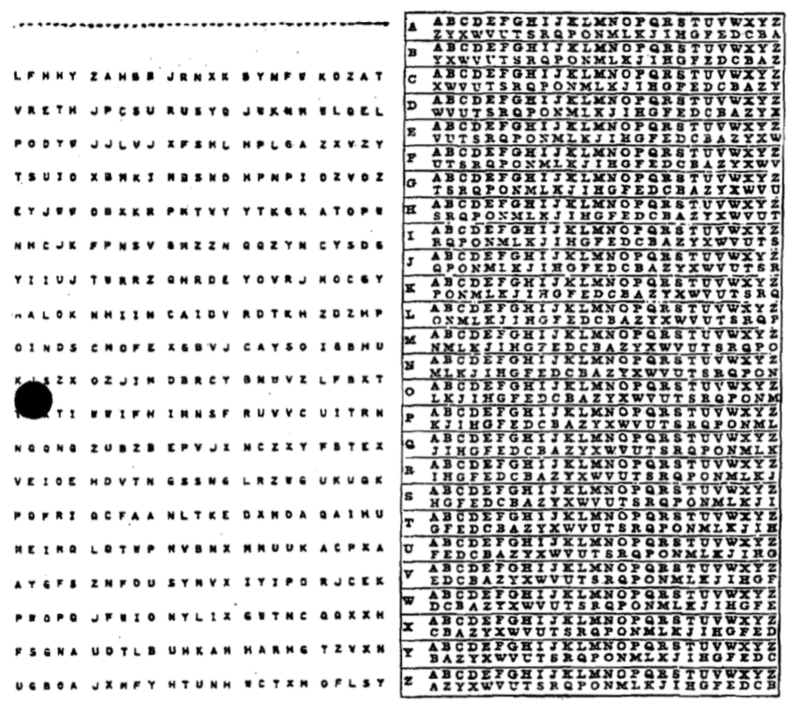
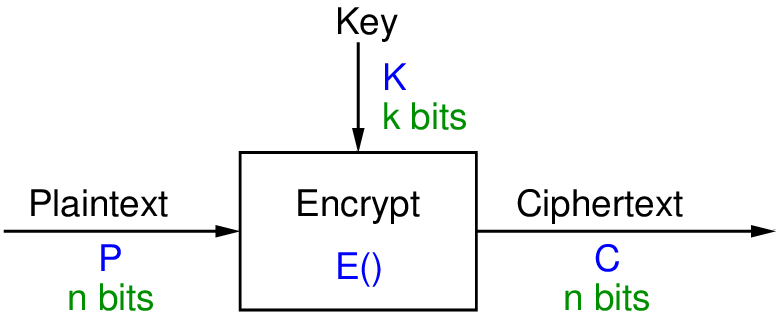
A Comparison of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish for Guessing Attacks Prevention

Computers | Free Full-Text | A Fast Text-to-Image Encryption-Decryption Algorithm for Secure Network Communication | HTML

A Comparison of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish for Guessing Attacks Prevention