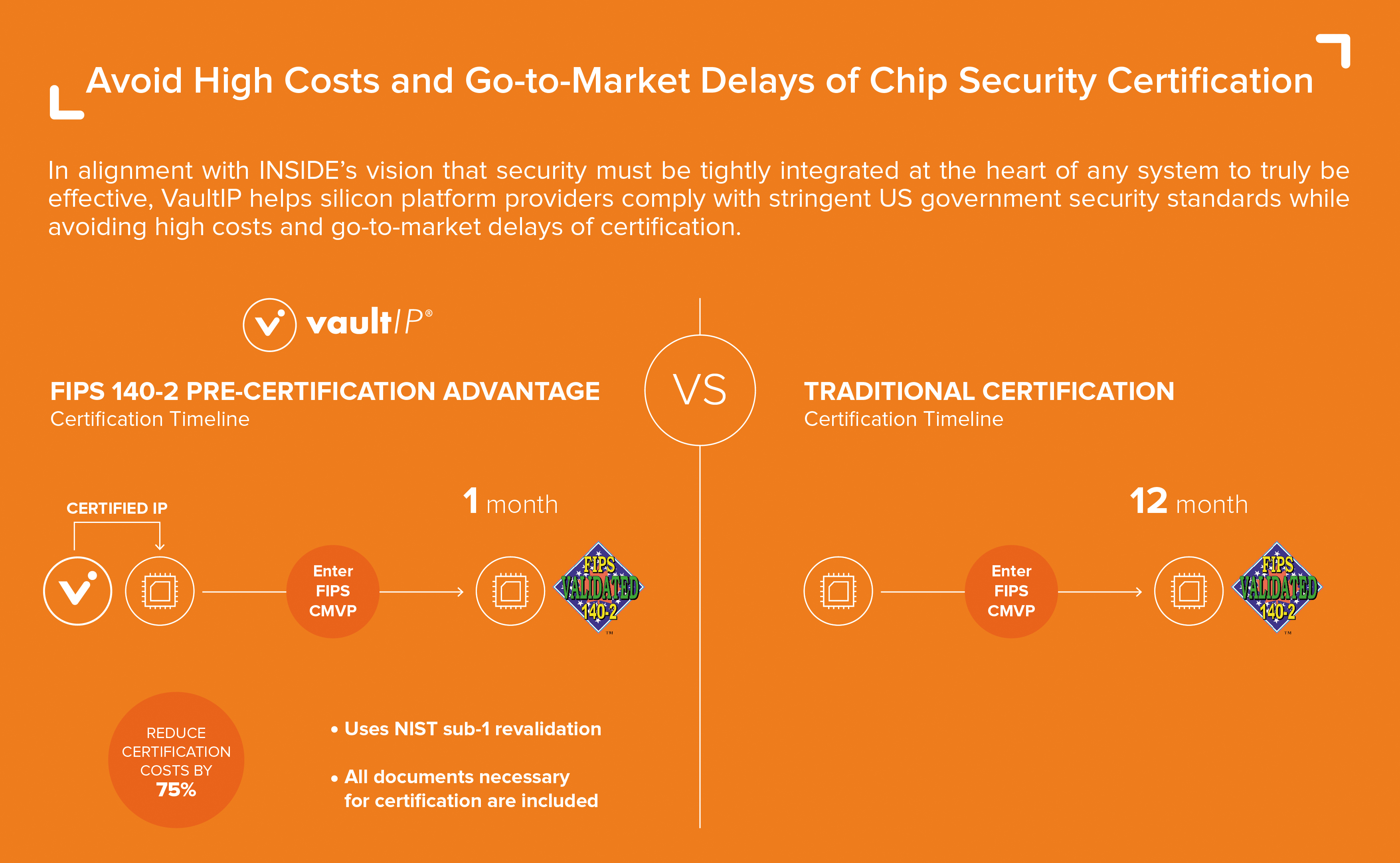
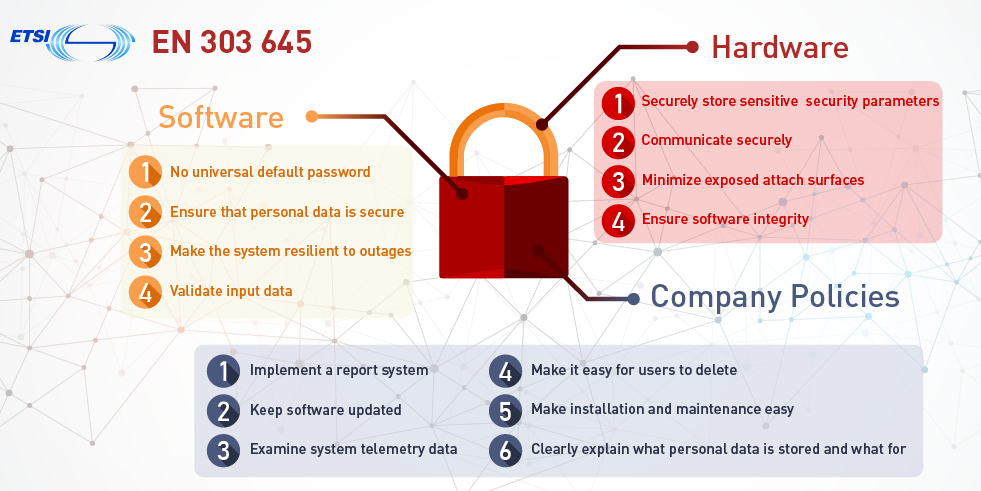
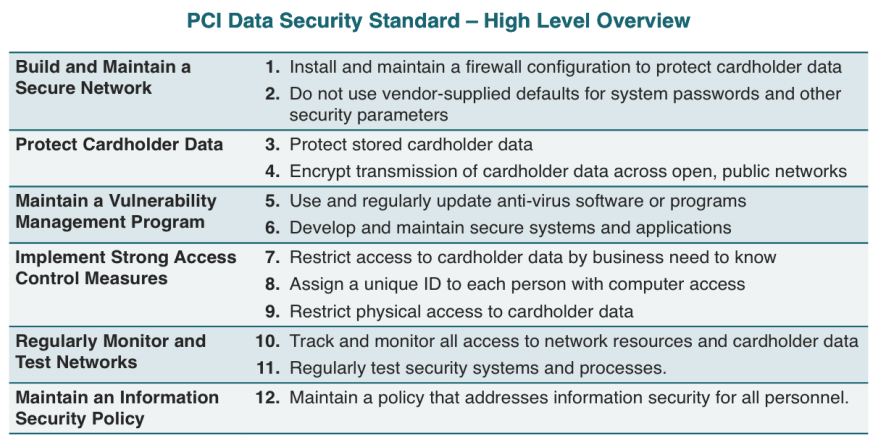
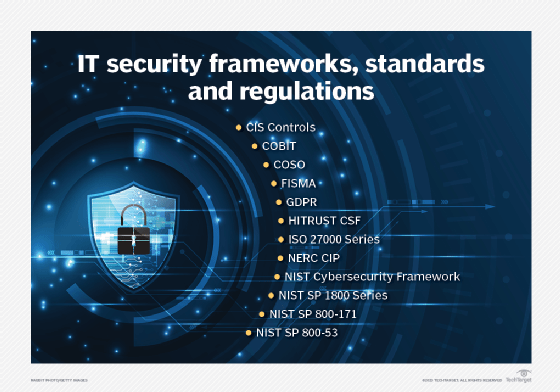
INKA Entworks Receives Multiple ISO Certifications; Affirms Commitment To Highest Security Standards Providing Robust App And Cloud Security Through AppSealing And PallyCon - Inka Entworks

تويتر \ Survio Official على تويتر: "We are exited to announce that https://t.co/CNxLUjjwEV has just achieved ISO 27001:2013 certification. Our long-term goal is to provide high quality services, following high security standards.