Electronics | Free Full-Text | Toward Developing Efficient Conv-AE-Based Intrusion Detection System Using Heterogeneous Dataset | HTML
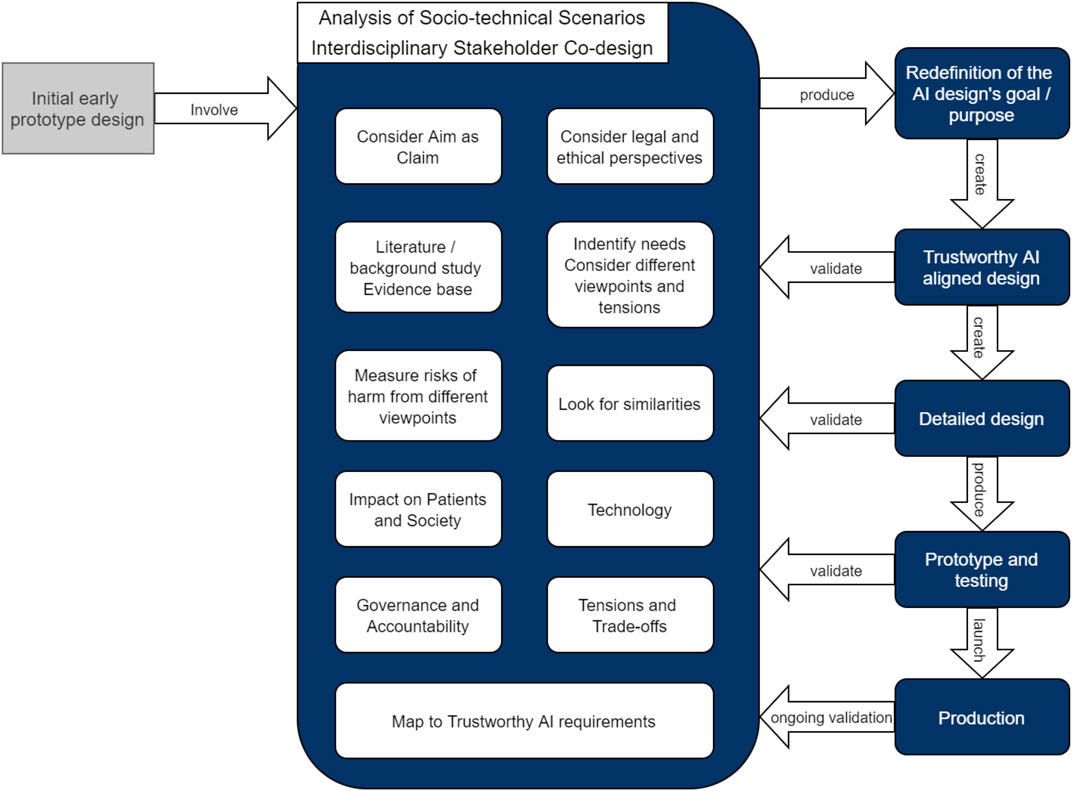
Frontiers | Co-Design of a Trustworthy AI System in Healthcare: Deep Learning Based Skin Lesion Classifier

LiXiongBao Glowing Alarm Clock 7 LED Color, Digital Alarm Thermometer Night Glowing Cube 7 Colors Clock LED Change LCD with Data and Temperature Display for Bedroom Child (Changeable Color) : Amazon.ca: Home

Anomaly‐based intrusion detection systems: The requirements, methods, measurements, and datasets - Hajj - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
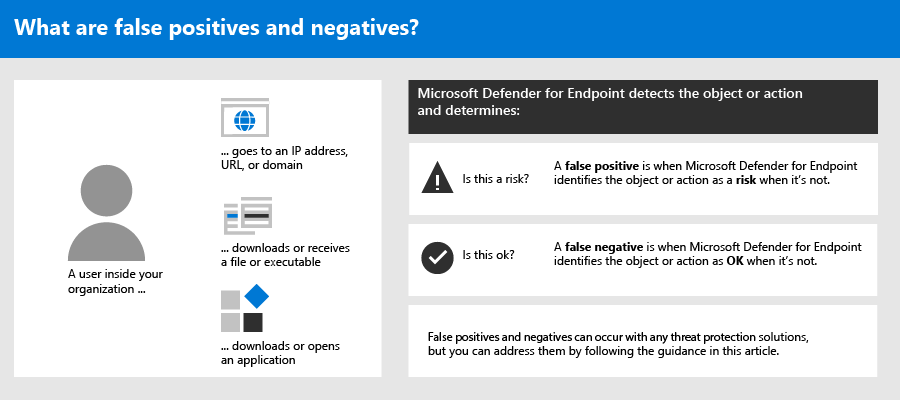
tempo make out rice ids design adjust settings common benign activities don't generate alarms - mrcuteanimals.com
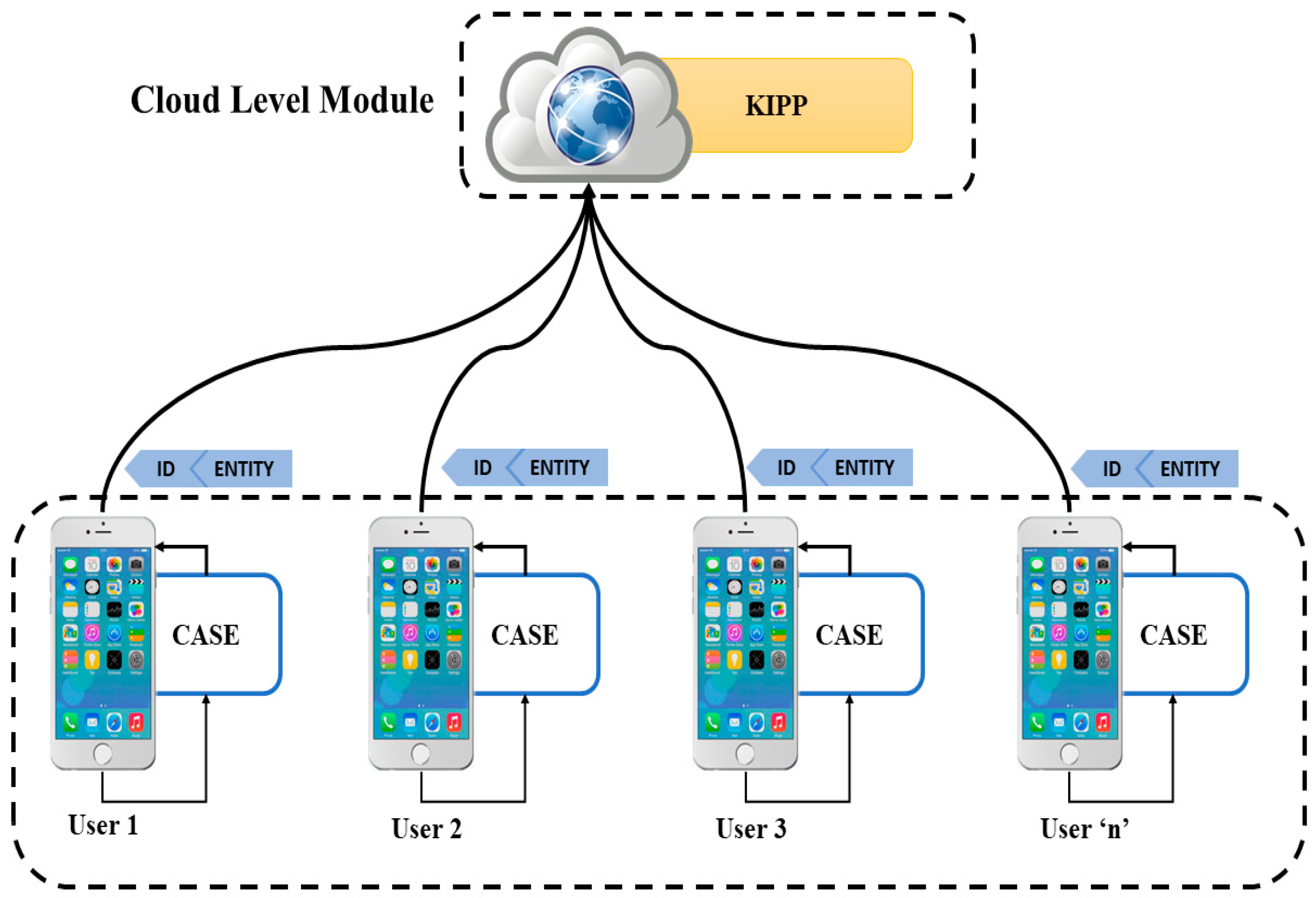
Applied Sciences | Free Full-Text | MaLang: A Decentralized Deep Learning Approach for Detecting Abusive Textual Content | HTML

What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security