CTF Generator: Low private exponent (d) in RSA … the Wiener attack | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
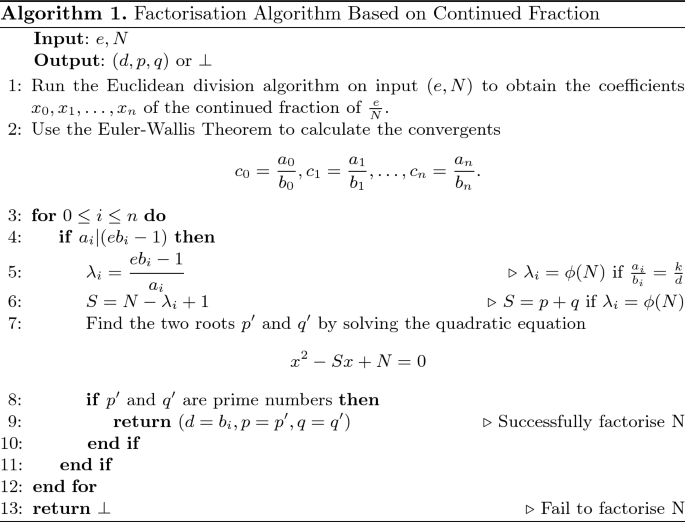
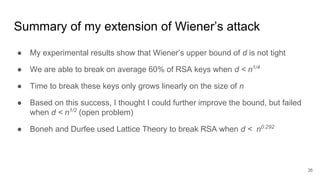
RSA: Continued Fractions — The Wiener Attack | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium