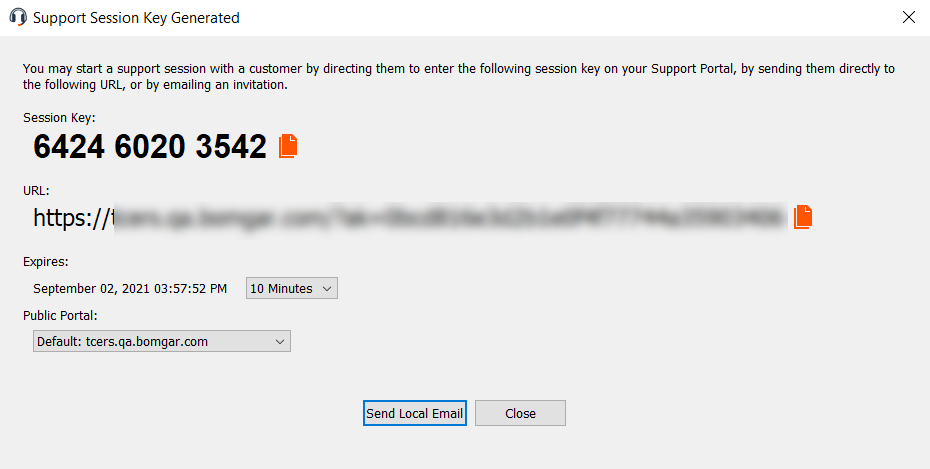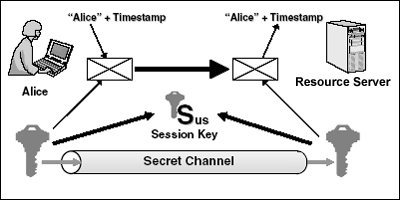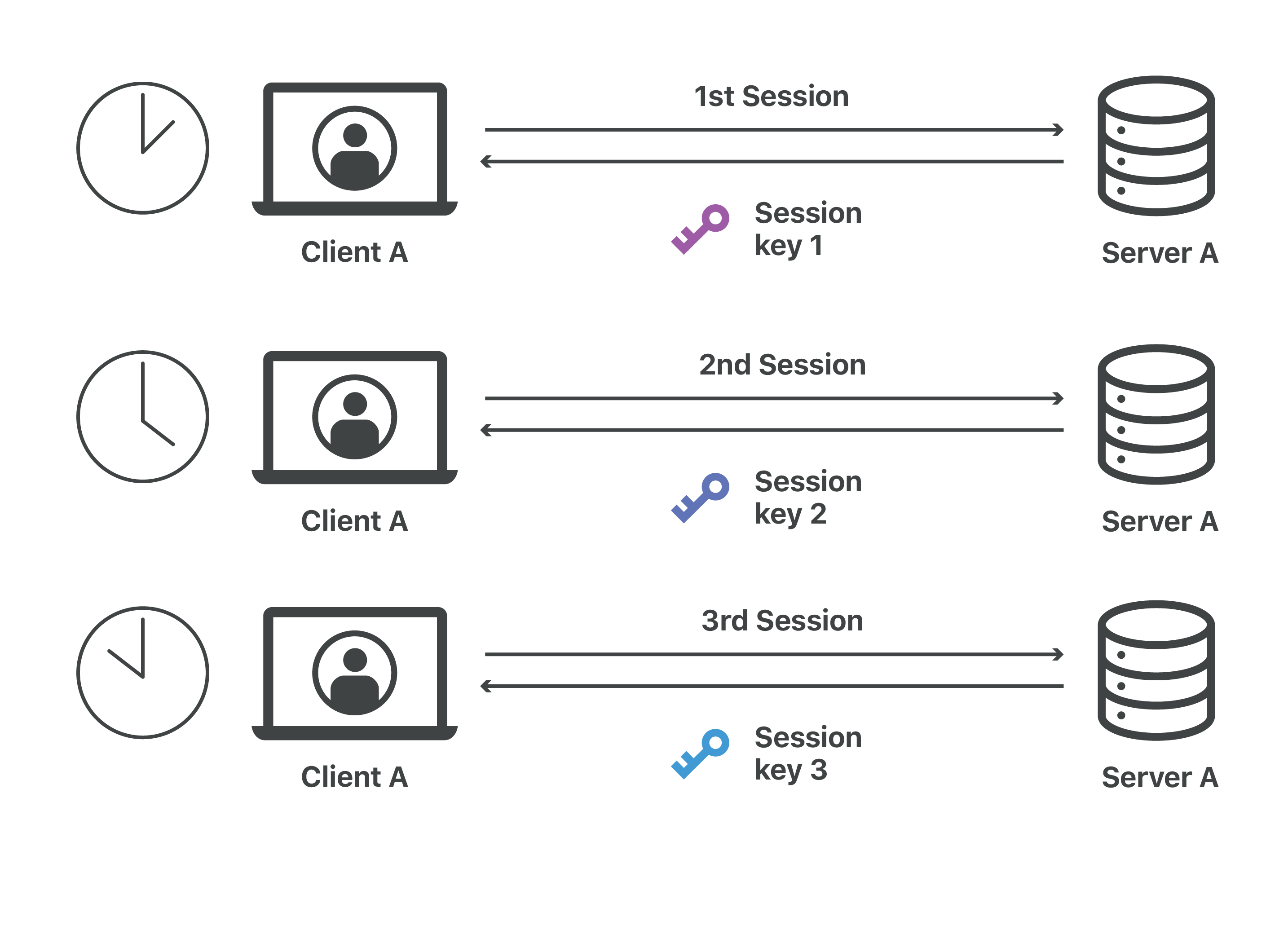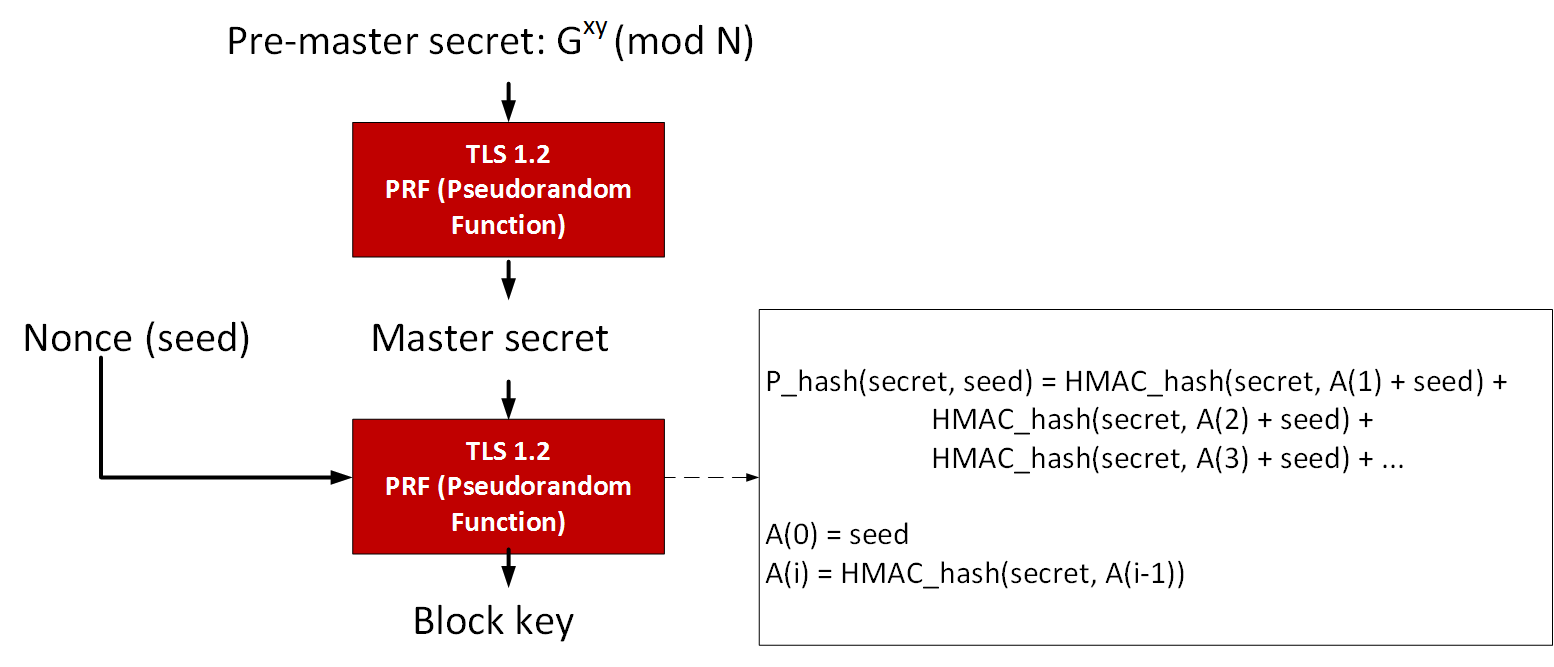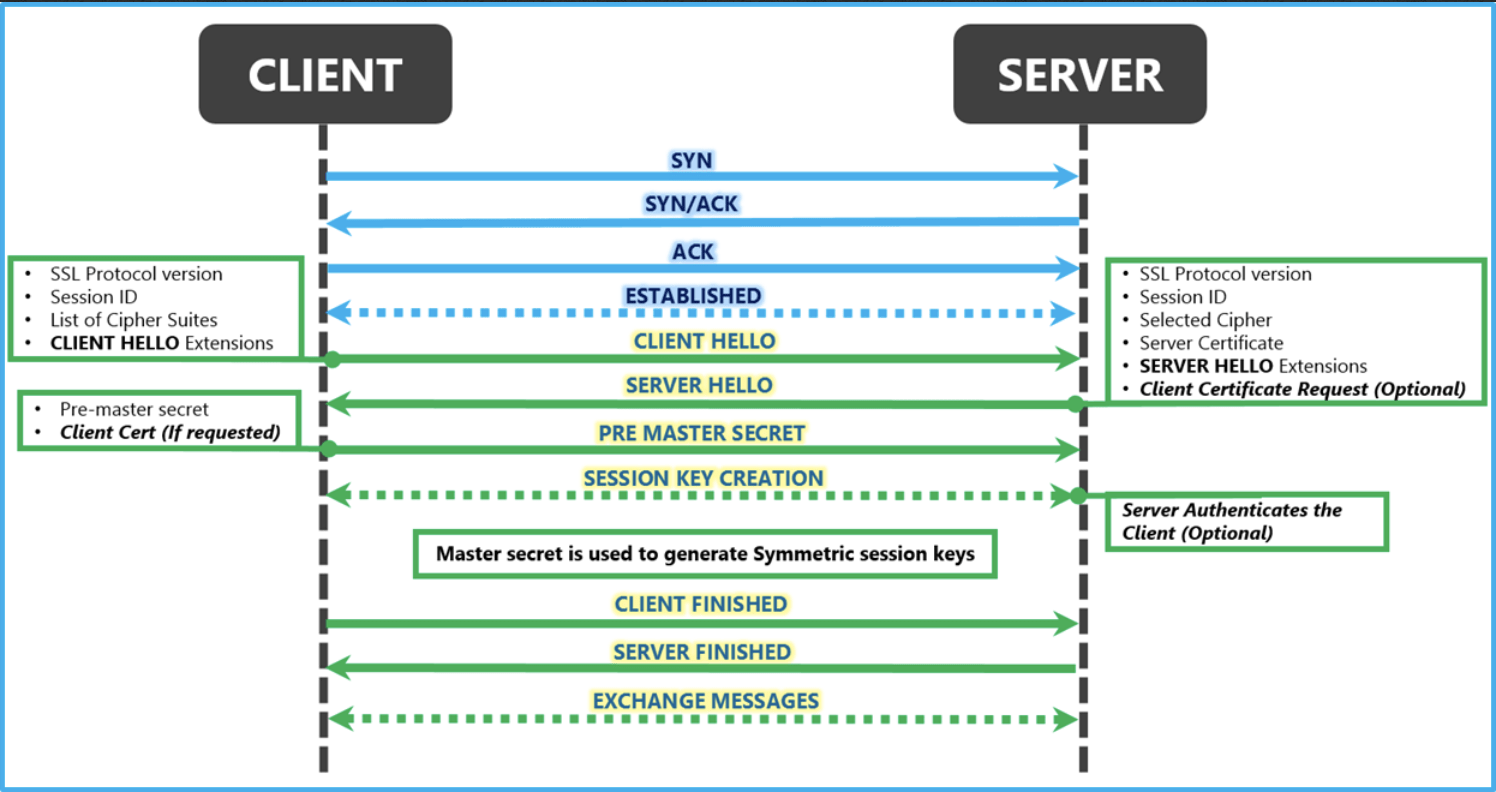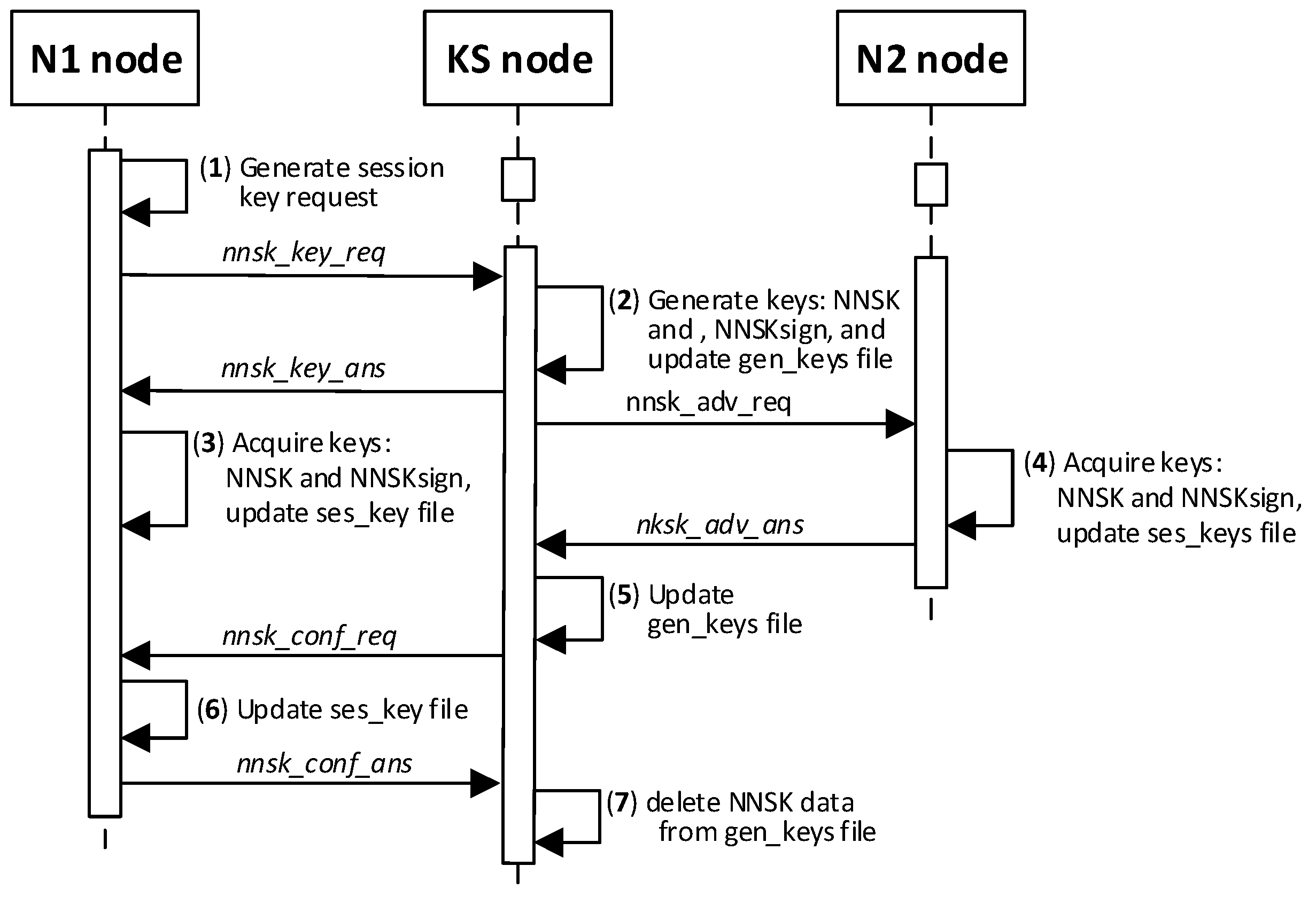
Sensors | Free Full-Text | Cryptographic Keys Generating and Renewing System for IoT Network Nodes—A Concept | HTML

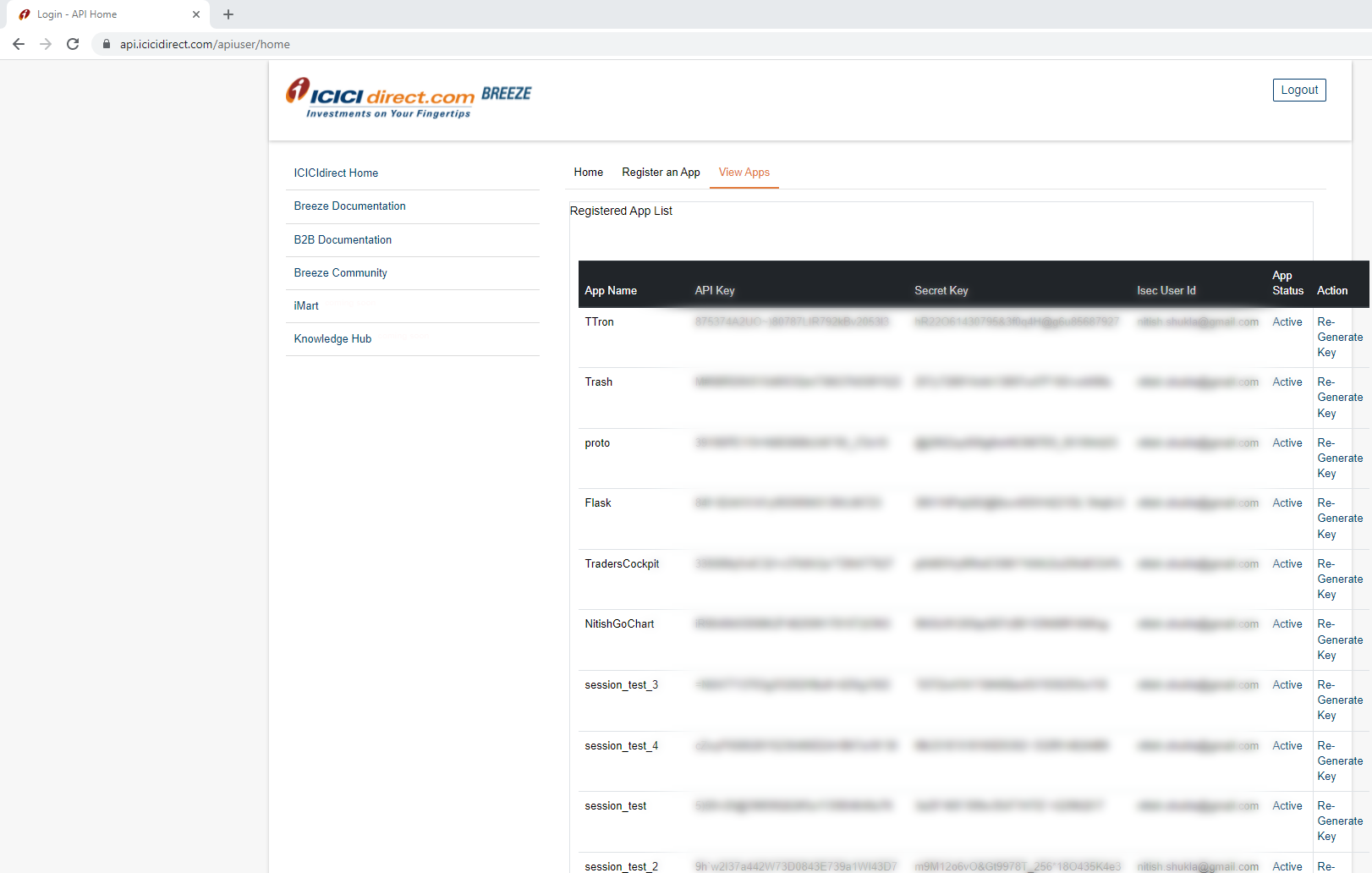
Application Session Key in Application Server doesn't match device generated - ChirpStack Application Server - ChirpStack Community Forum