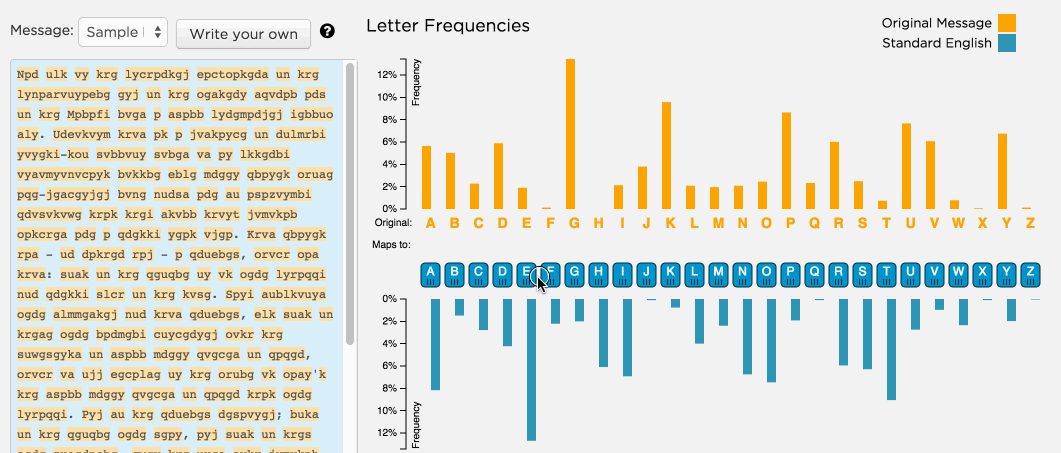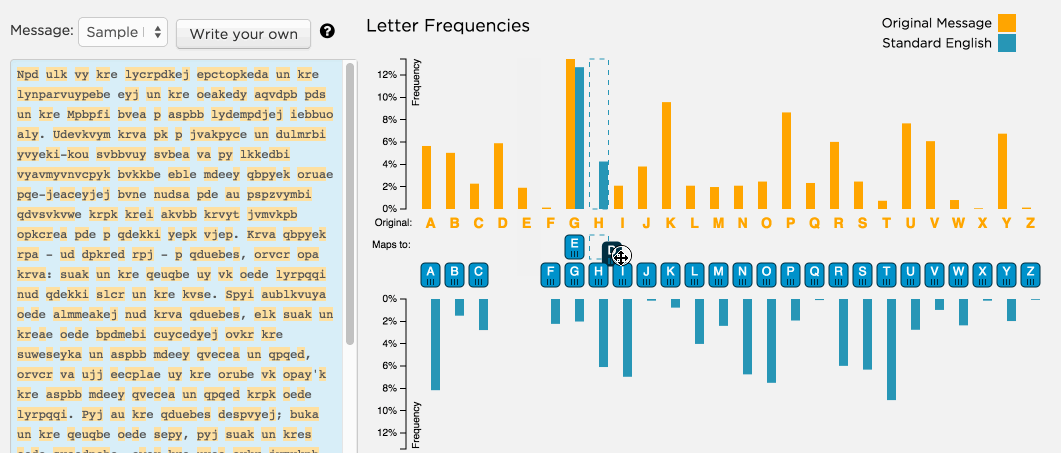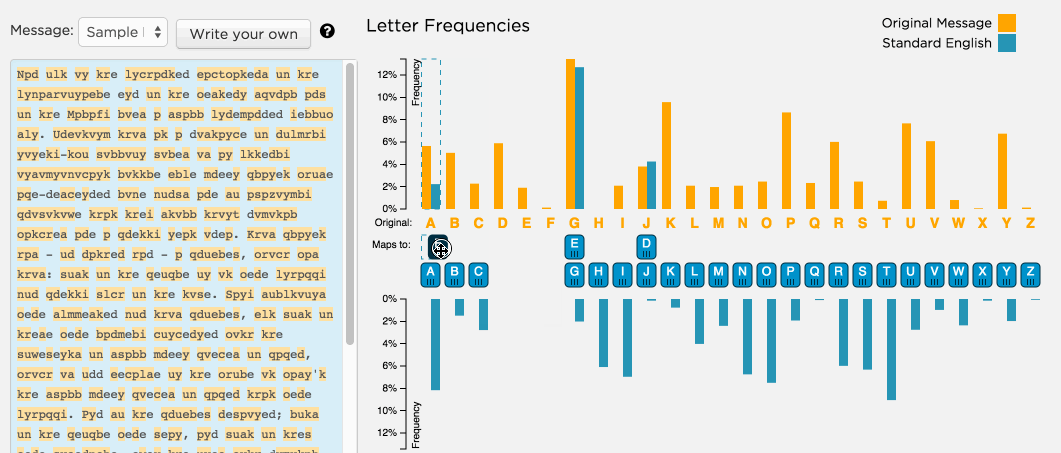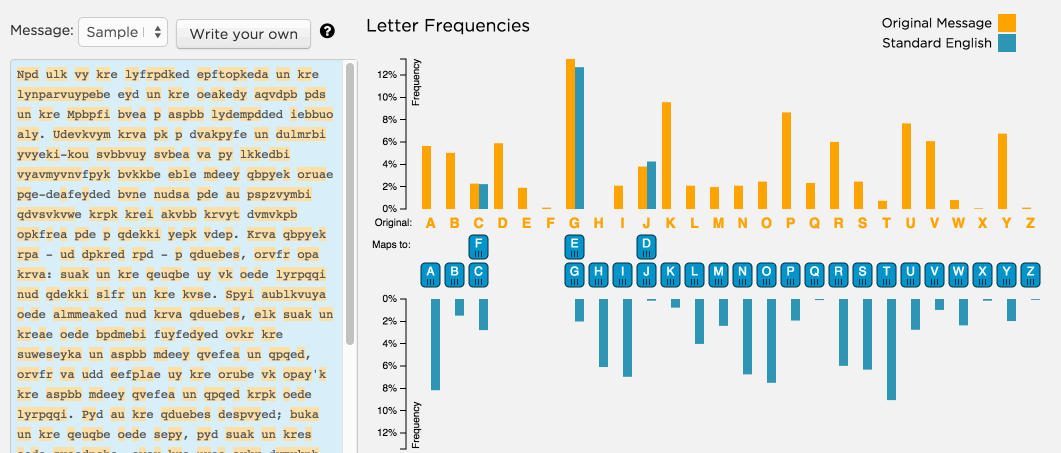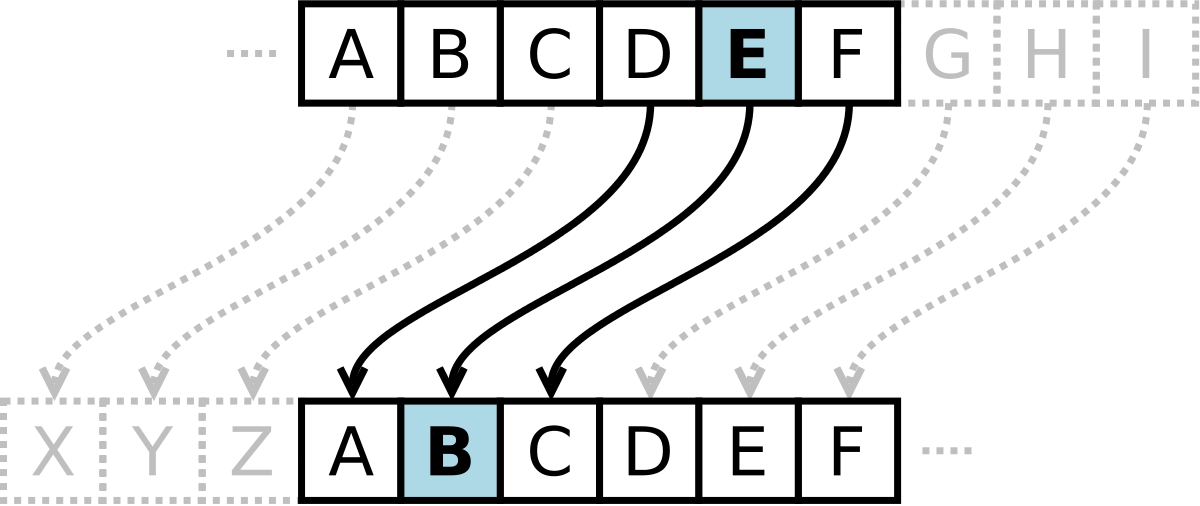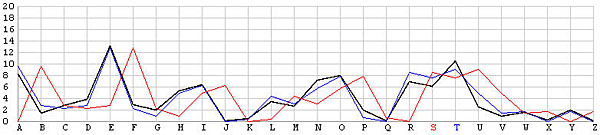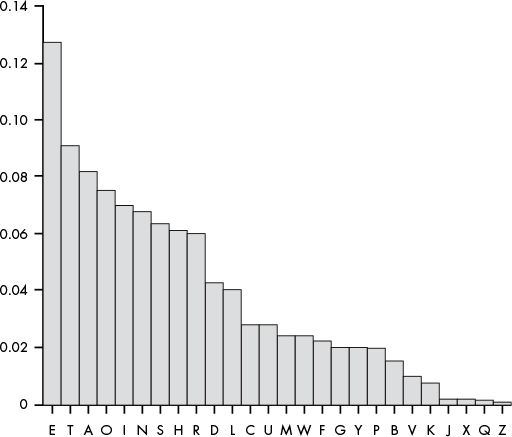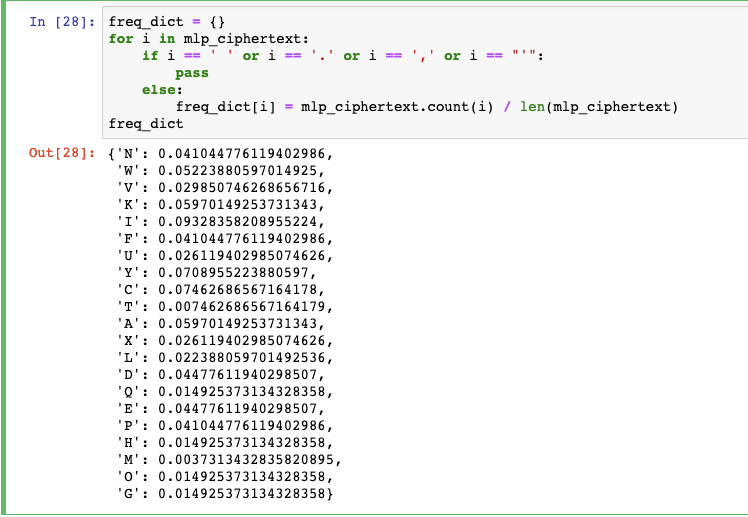
Breaking My Little Pony: Frequency Analysis for Breaking Ciphers | by Jonathan Keller | Towards Data Science
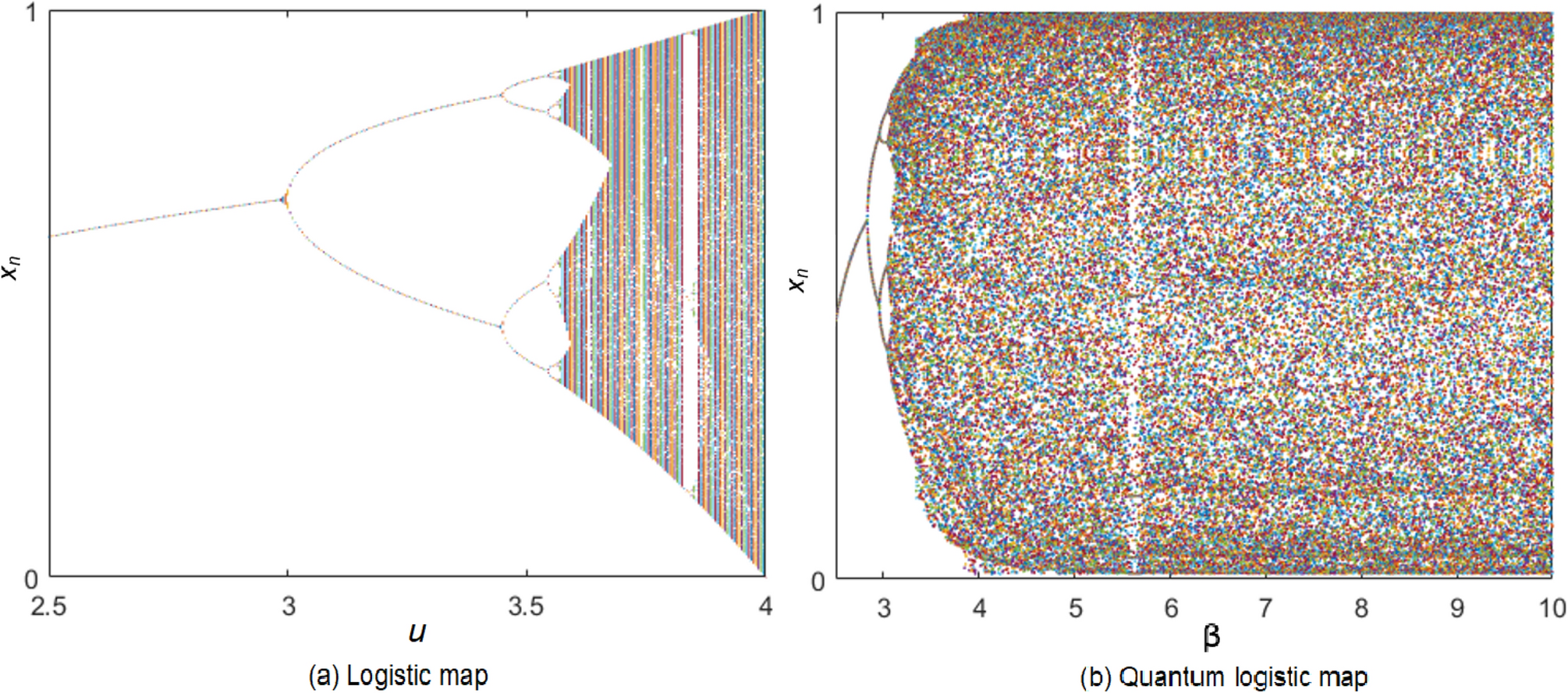
An image encryption scheme based on public key cryptosystem and quantum logistic map | Scientific Reports

Monitoring data encryption method for howitzer shell transfer arm using chaos and compressive sensing - Xi Liu, Baolin Hou, Qiangqiang Zhao, 2019

Energies | Free Full-Text | Continuously Variable-Frequency Energy-Encrypted Wireless Power Transfer | HTML