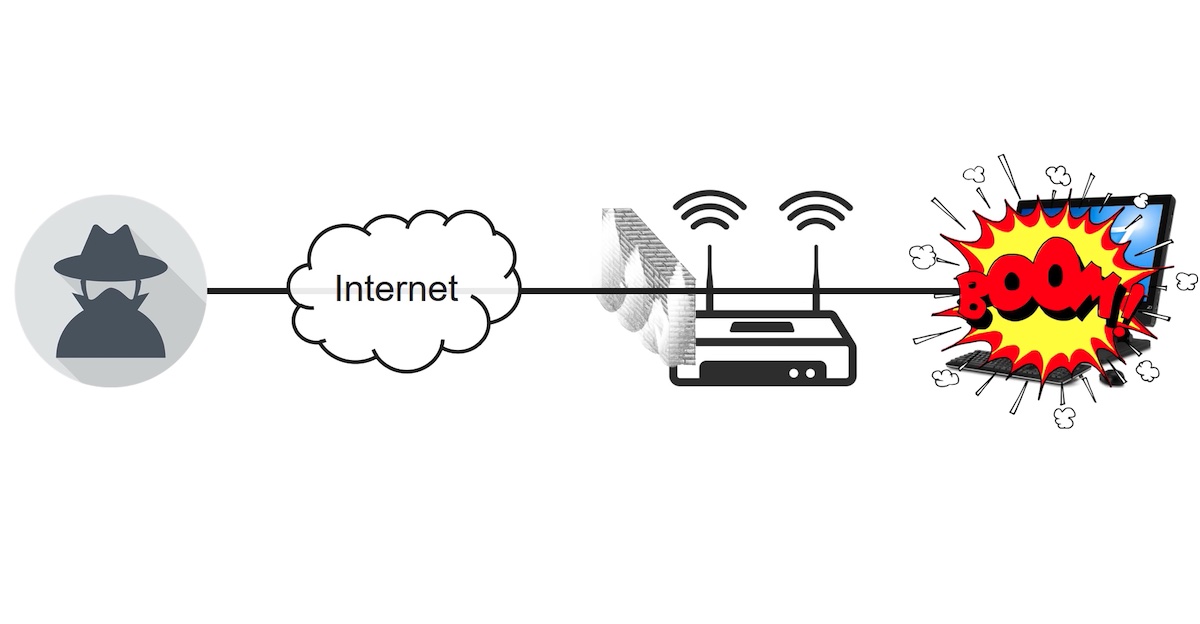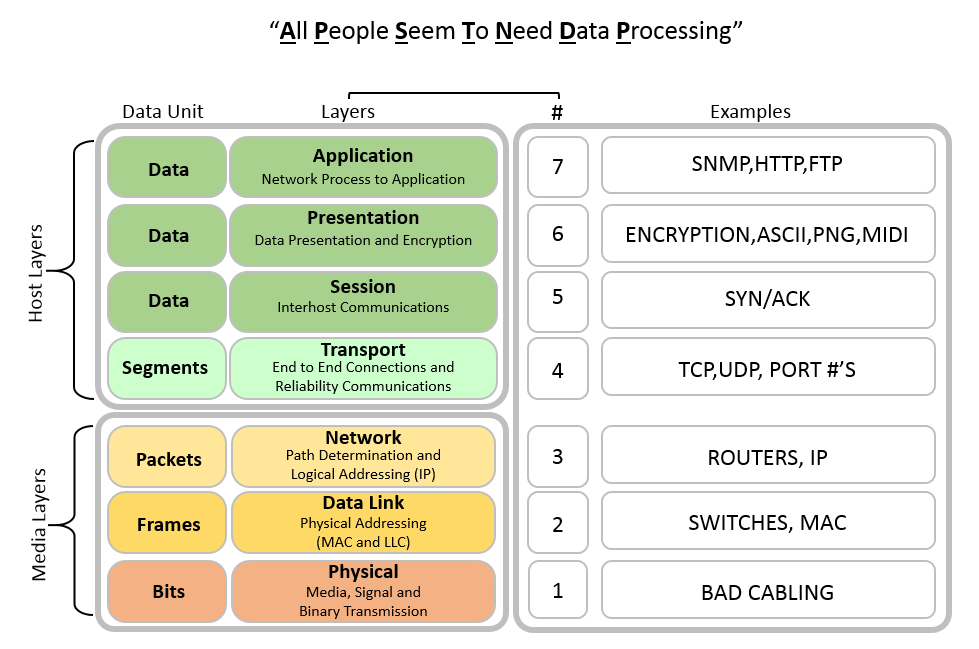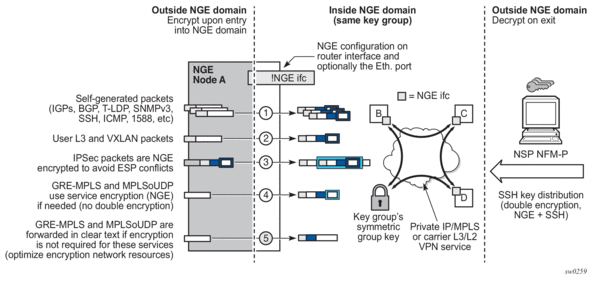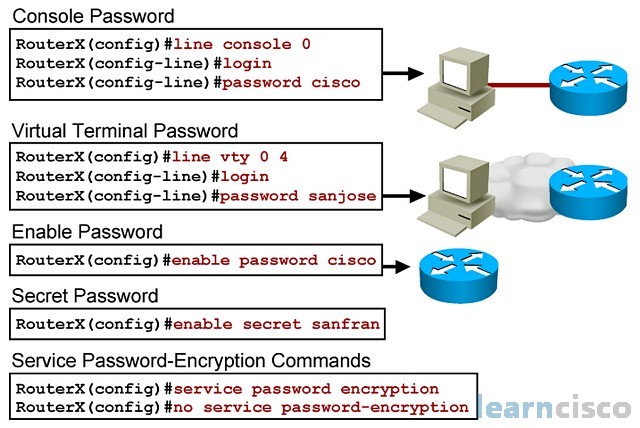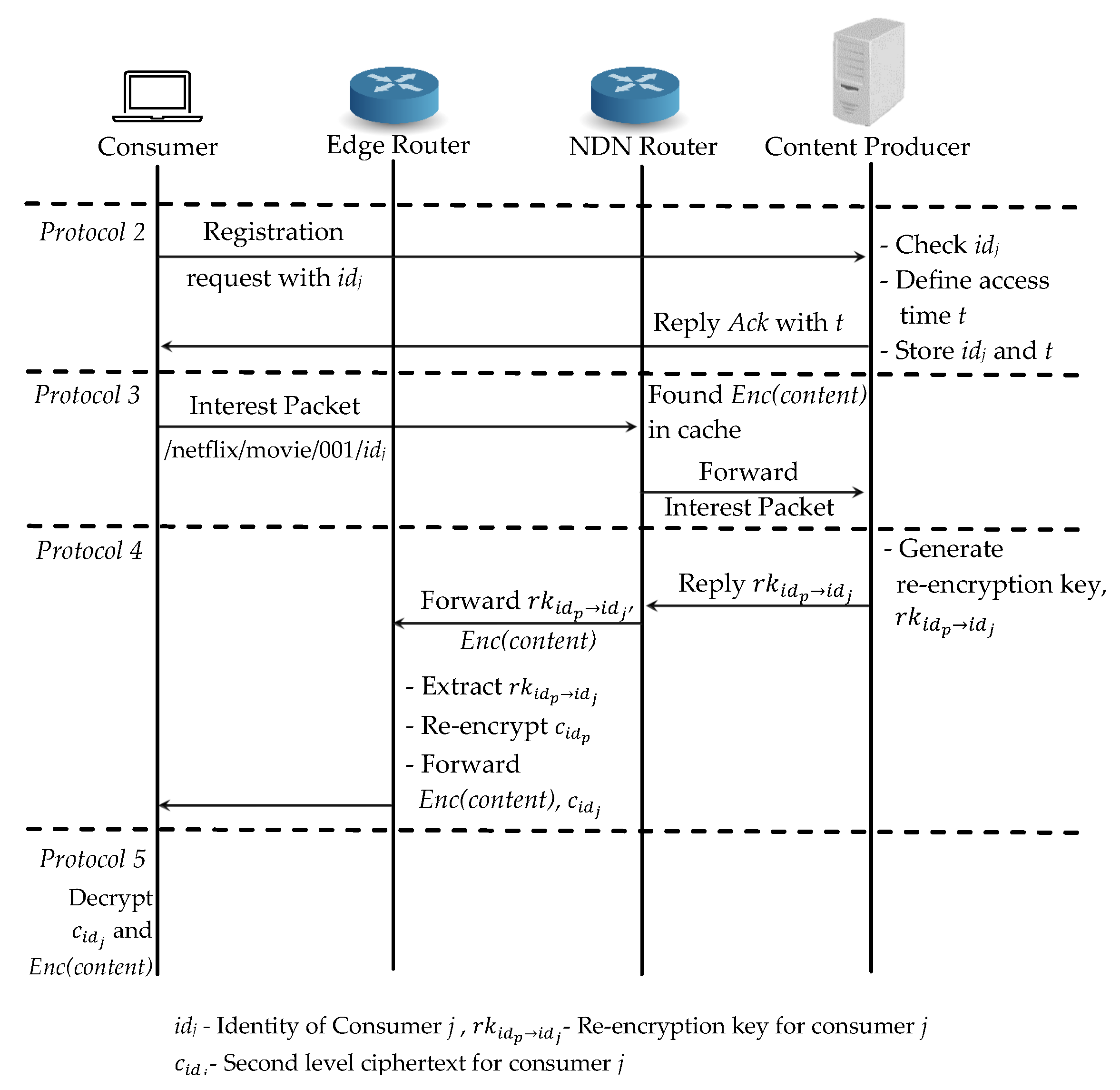
Sensors | Free Full-Text | Secure Content Distribution with Access Control Enforcement in Named Data Networking | HTML
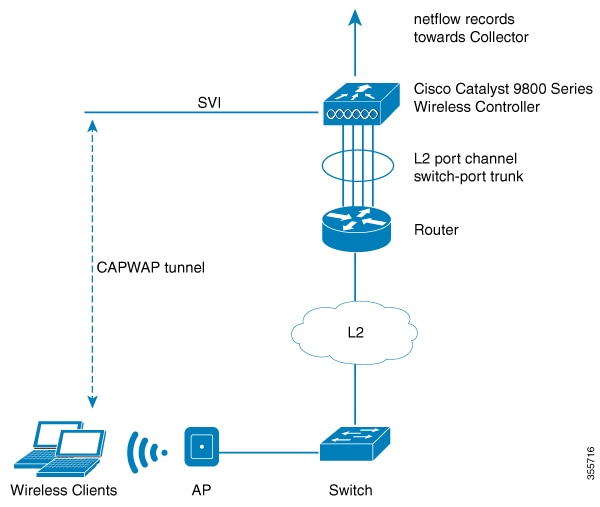
Cisco Content Hub - Configuring Encrypted Traffic Analytics on Software Defined Access (SDA-Wireless)

Encrypted packets with commonly used protection mechanisms. When HTTPS... | Download High-Resolution Scientific Diagram
![Security Configuration Guide for vEdge Routers, Cisco SD-WAN Releases 19.1, 19.2, and 19.3 - Security Overview [Cisco SD-WAN] - Cisco Security Configuration Guide for vEdge Routers, Cisco SD-WAN Releases 19.1, 19.2, and 19.3 - Security Overview [Cisco SD-WAN] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/360001-370000/368001-369000/368448.jpg)






:max_bytes(150000):strip_icc()/SynologyRT2600AC-593074863df78c08abf633bc.jpg)