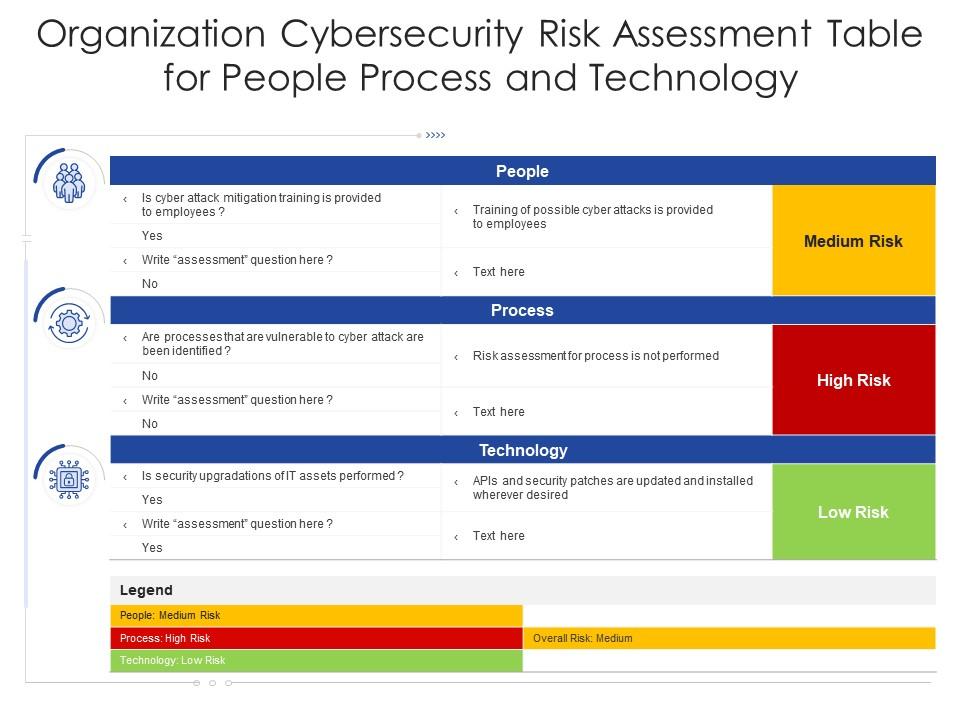
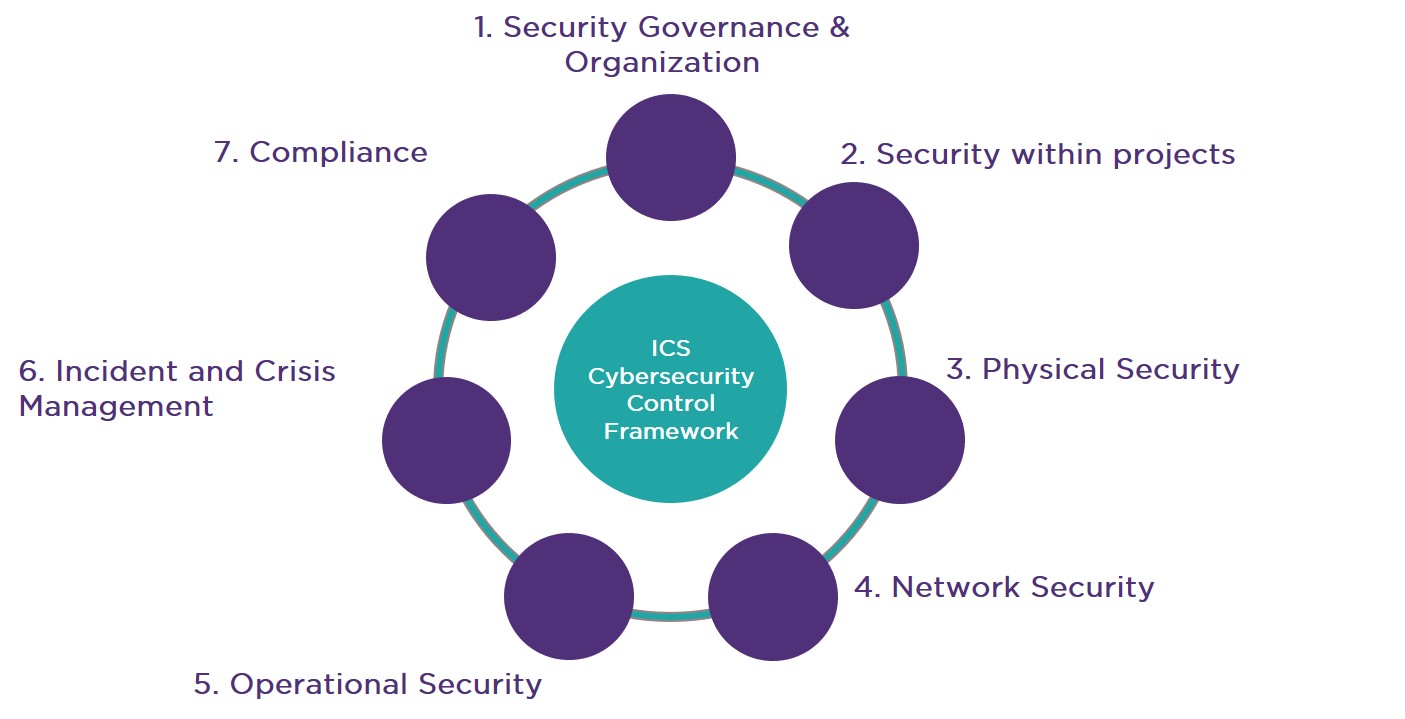
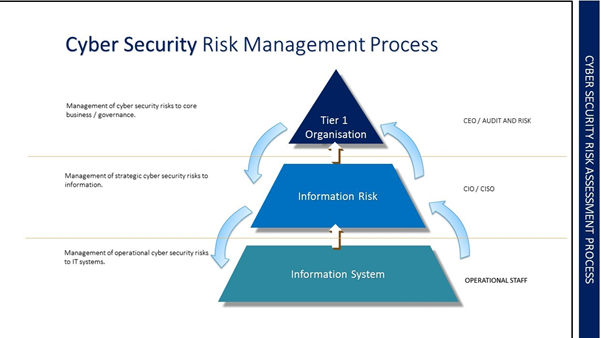
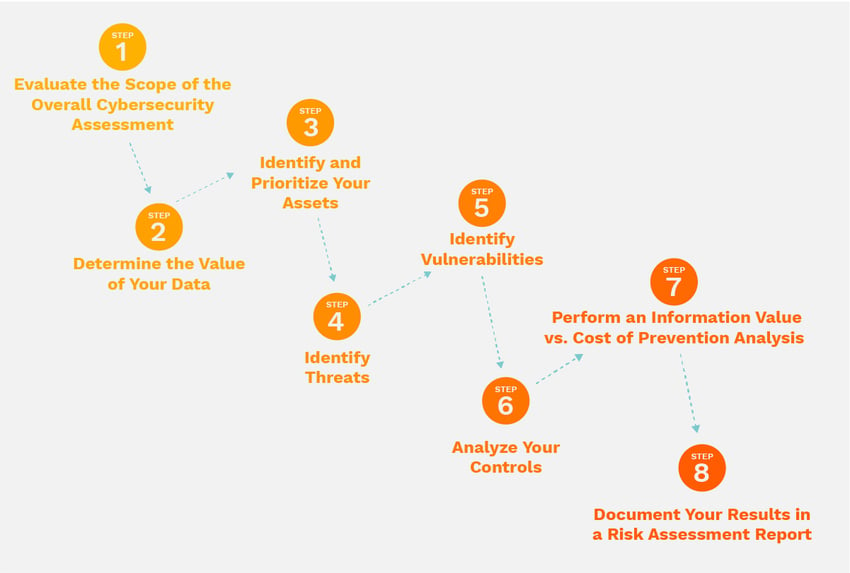
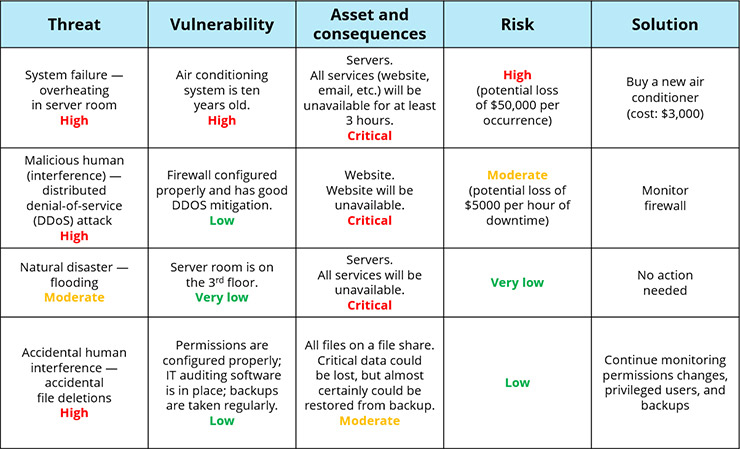
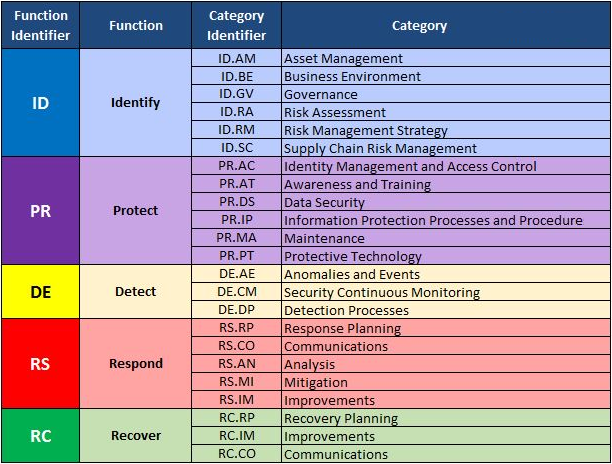
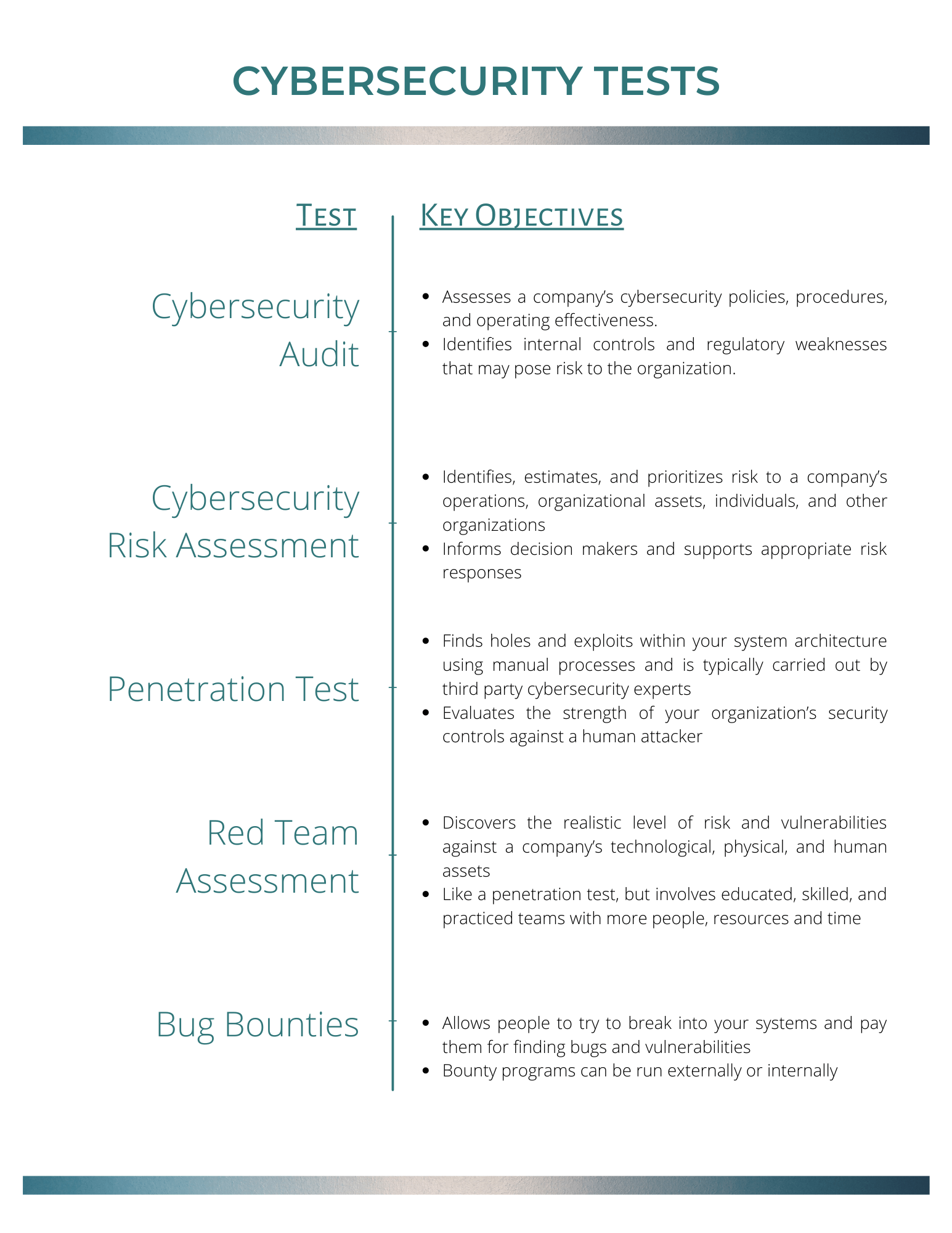
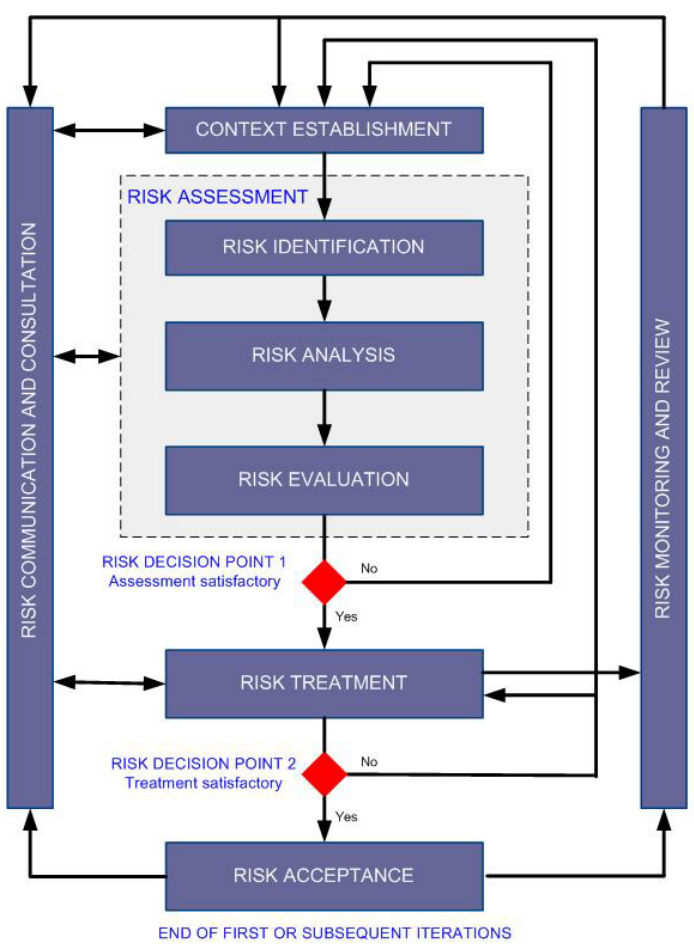
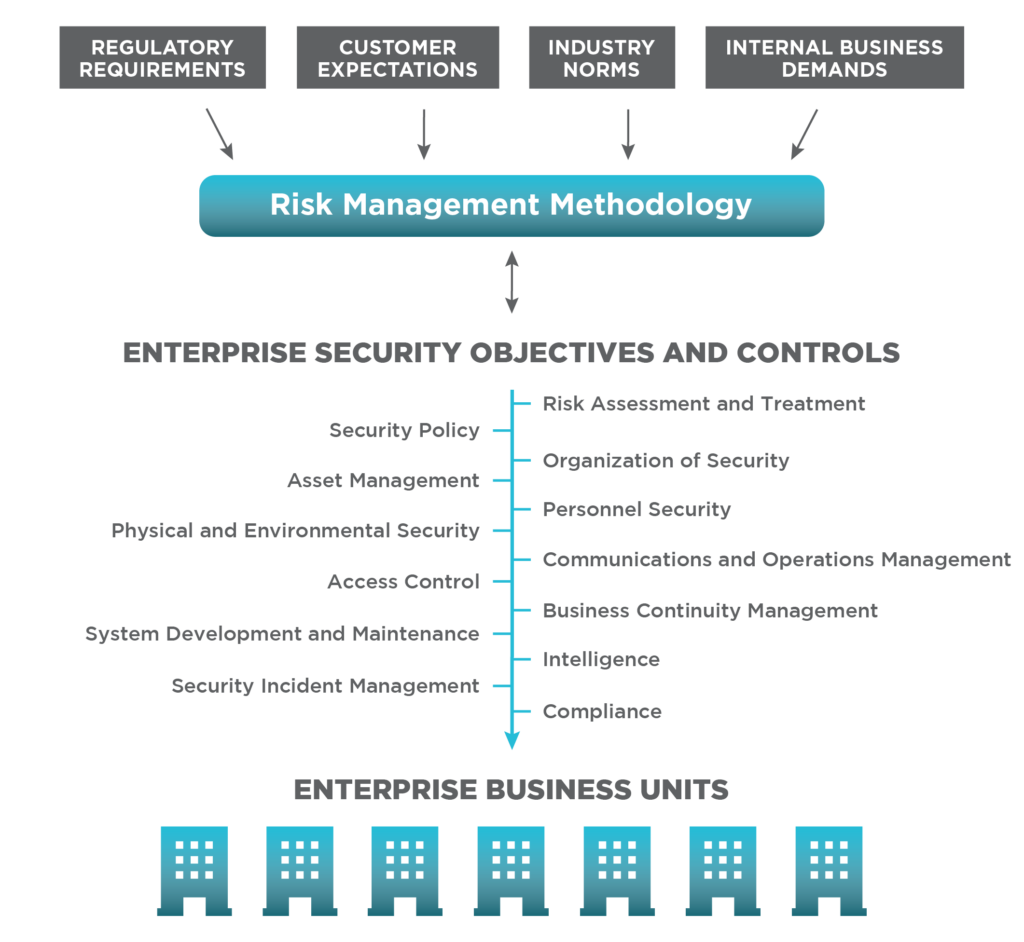
Cybersecurity Risk Assessment Chart For Organization | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
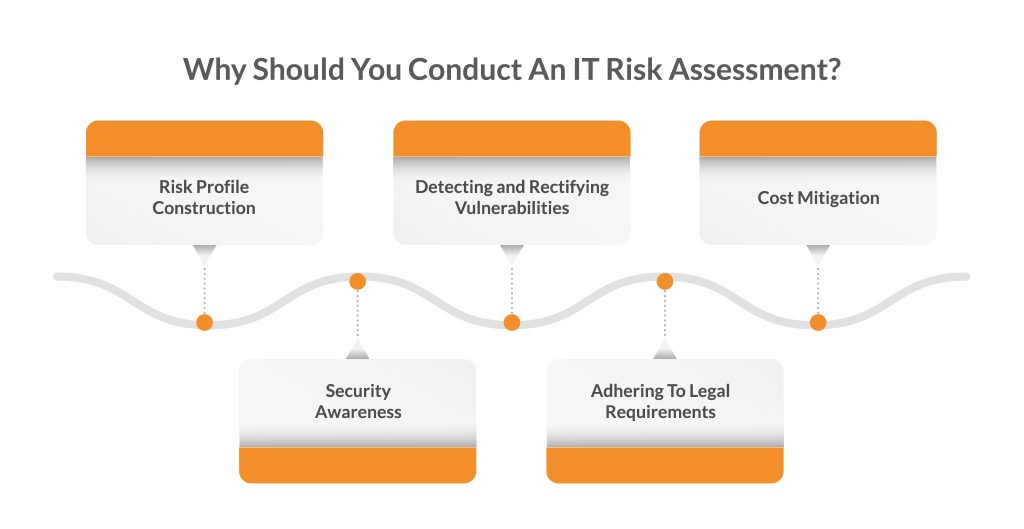
Risk Assessment: The Crucial Element Of A Successful Security Implementation Program - Security Boulevard
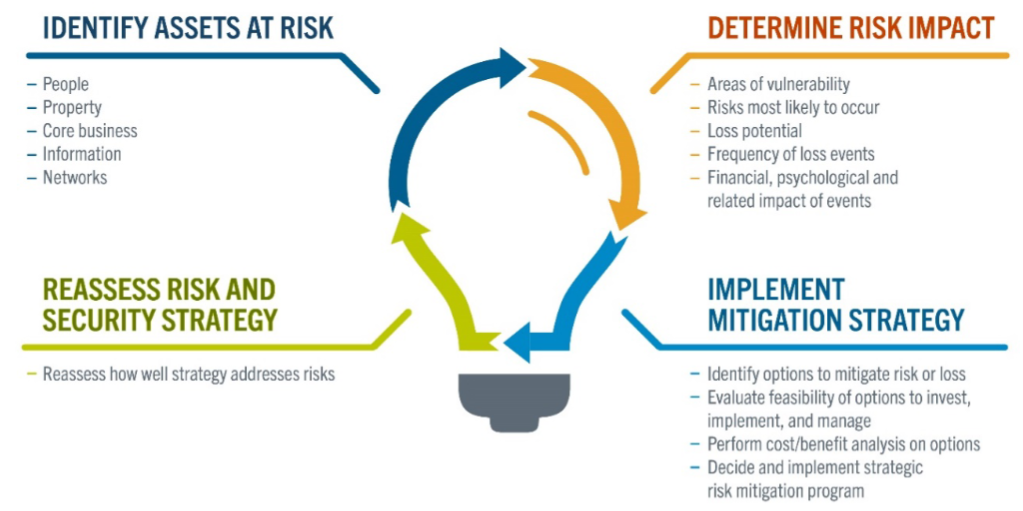
Options for In-House Security: How to Determine Which Approach is Right for Your Organization | Allied Universal