TS 133 246 - V11.1.0 - Universal Mobile Telecommunications System (UMTS); LTE; 3G Security; Security of Multimedia Broadcast/Mul
TS 133 246 - V8.3.0 - Universal Mobile Telecommunications System (UMTS); LTE; 3G Security; Security of Multimedia Broadcast/Mult
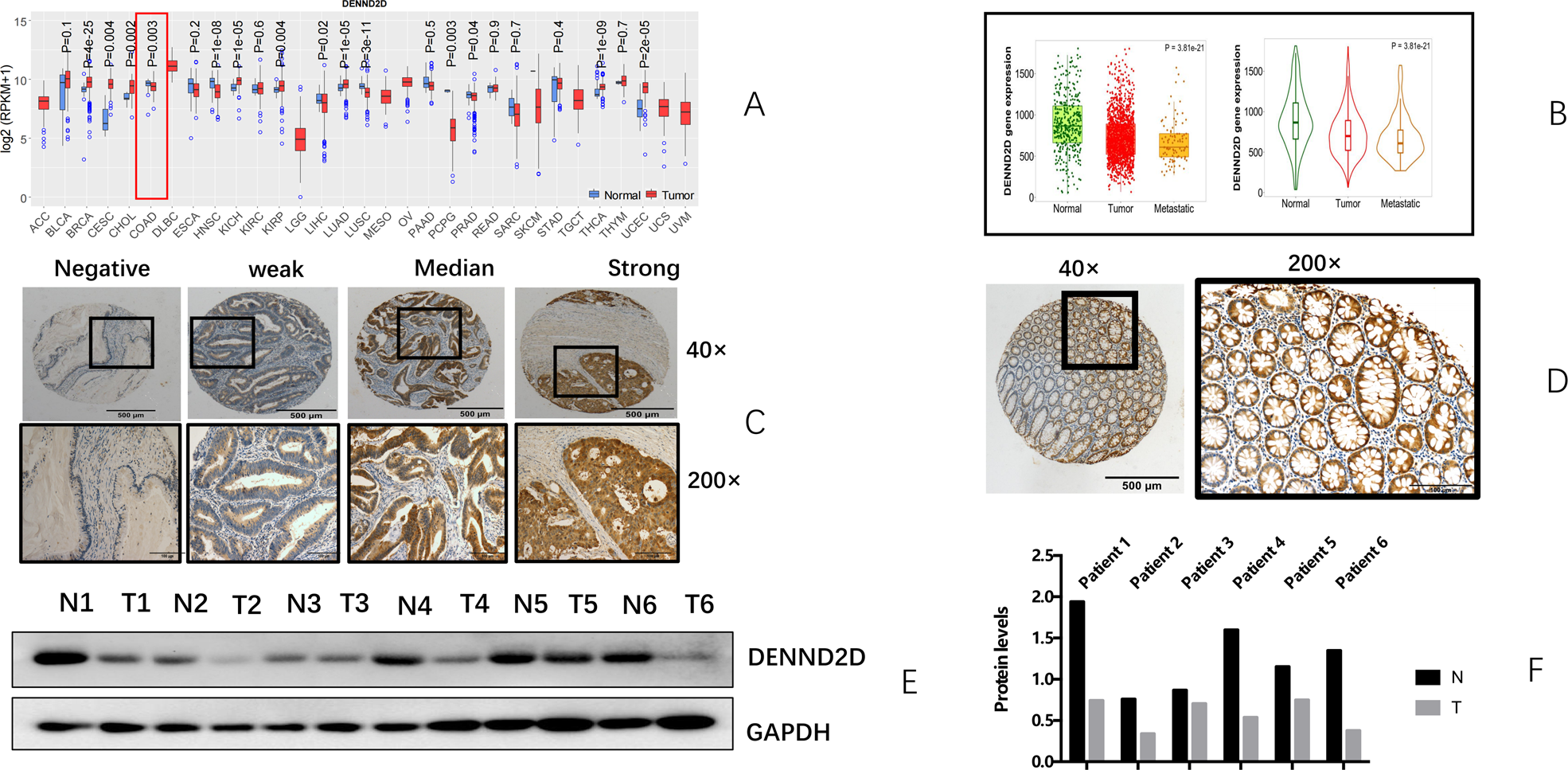
Stage IV colon cancer patients without DENND2D expression benefit more from neoadjuvant chemotherapy | Cell Death & Disease

SNORA23 inhibits HCC tumorigenesis by impairing the 2′-O-ribose methylation level of 28S rRNA | Cancer Biology & Medicine

Efficient derivation of human trophoblast stem cells from primed pluripotent stem cells | Science Advances

Security notions for stateful signature schemes - Yuan - 2022 - IET Information Security - Wiley Online Library

PDF) A Comparative Analysis of Various Cryptographic Algorithms Ensuring Secrecy and Authenticity of Exchanged Information

Security notions for stateful signature schemes - Yuan - 2022 - IET Information Security - Wiley Online Library

Security notions for stateful signature schemes - Yuan - 2022 - IET Information Security - Wiley Online Library
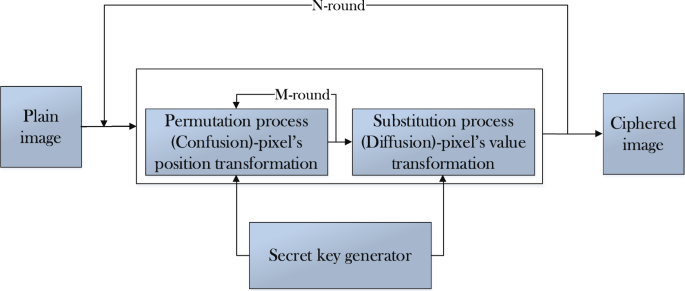
A Lightweight Chaos-Based Medical Image Encryption Scheme Using Random Shuffling and XOR Operations | SpringerLink
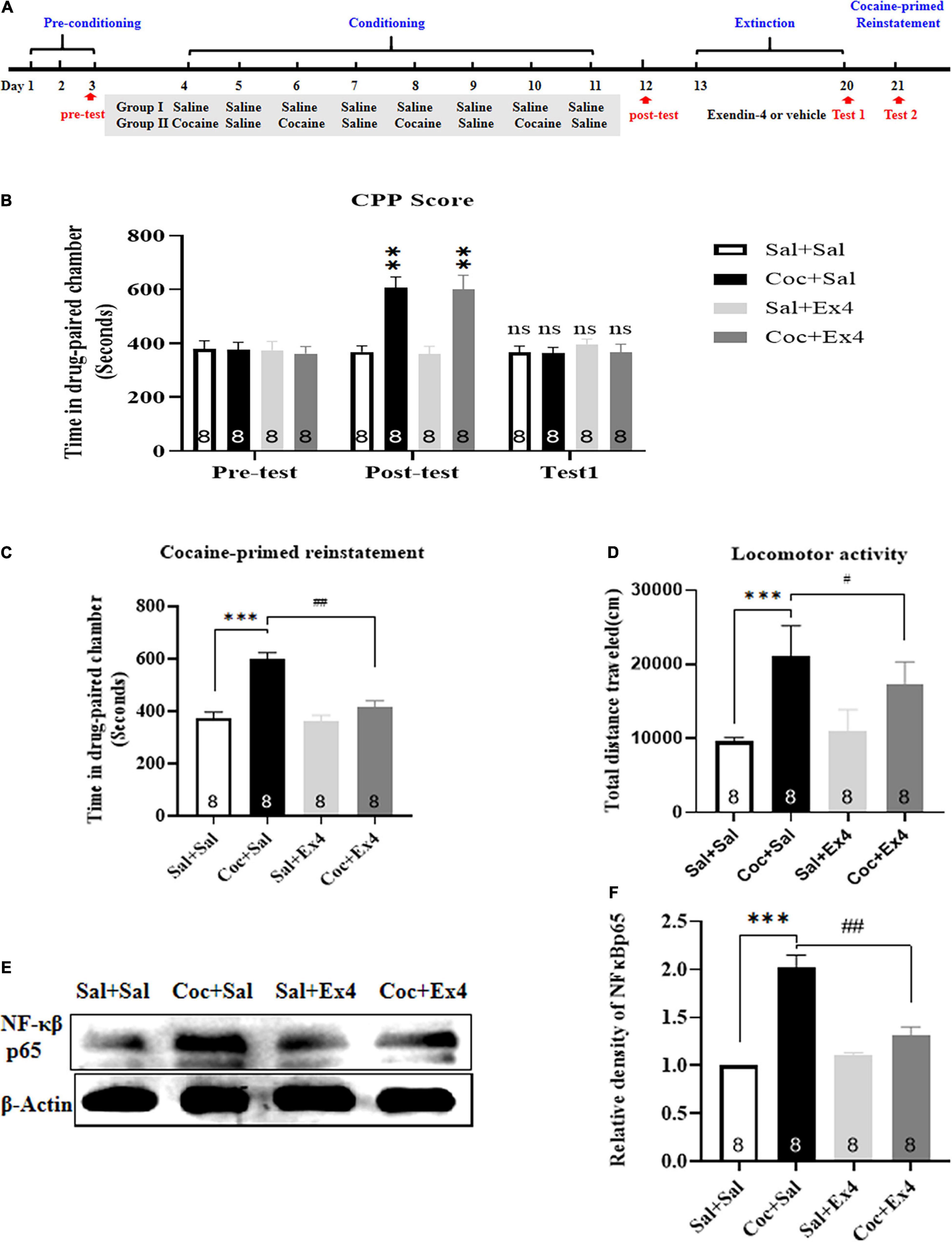
Frontiers | Effects of Glucagon-Like Peptide-1 Receptor Agonist Exendin-4 on the Reinstatement of Cocaine-Mediated Conditioned Place Preference in Mice

Security notions for stateful signature schemes - Yuan - 2022 - IET Information Security - Wiley Online Library
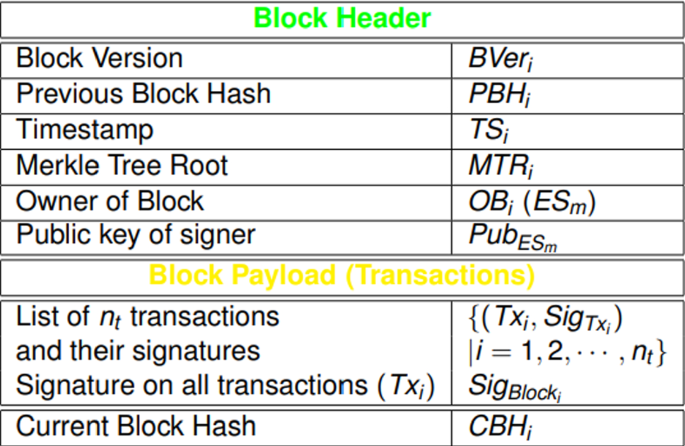
Blockchain-envisioned access control for internet of things applications: a comprehensive survey and future directions | SpringerLink
![A lightweight and secure online/offline cross-domain authentication scheme for VANET systems in Industrial IoT [PeerJ] A lightweight and secure online/offline cross-domain authentication scheme for VANET systems in Industrial IoT [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2021/cs-714/1/fig-4-full.png)





