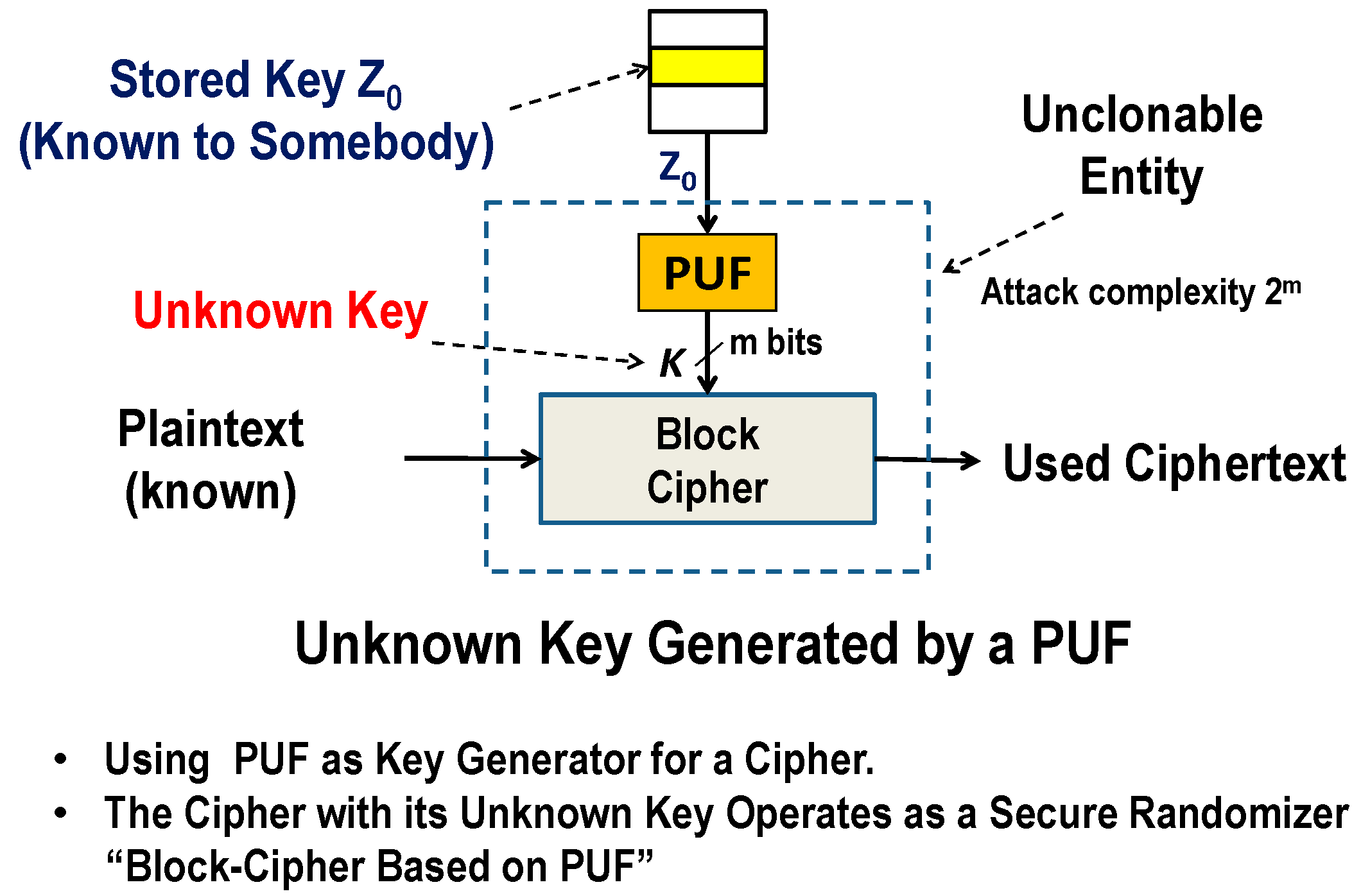
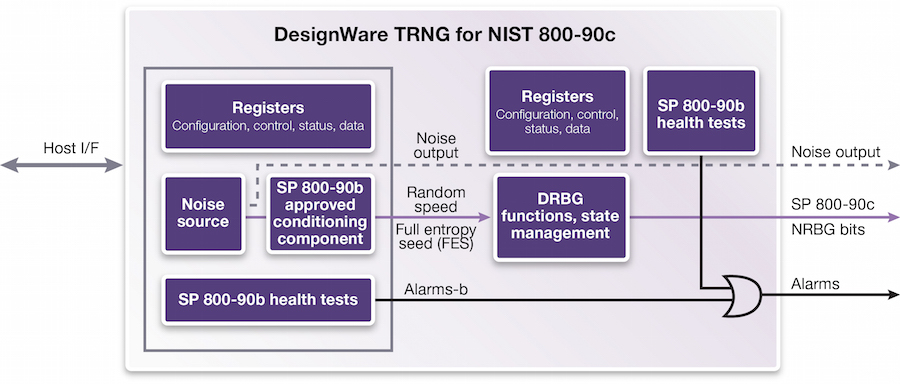
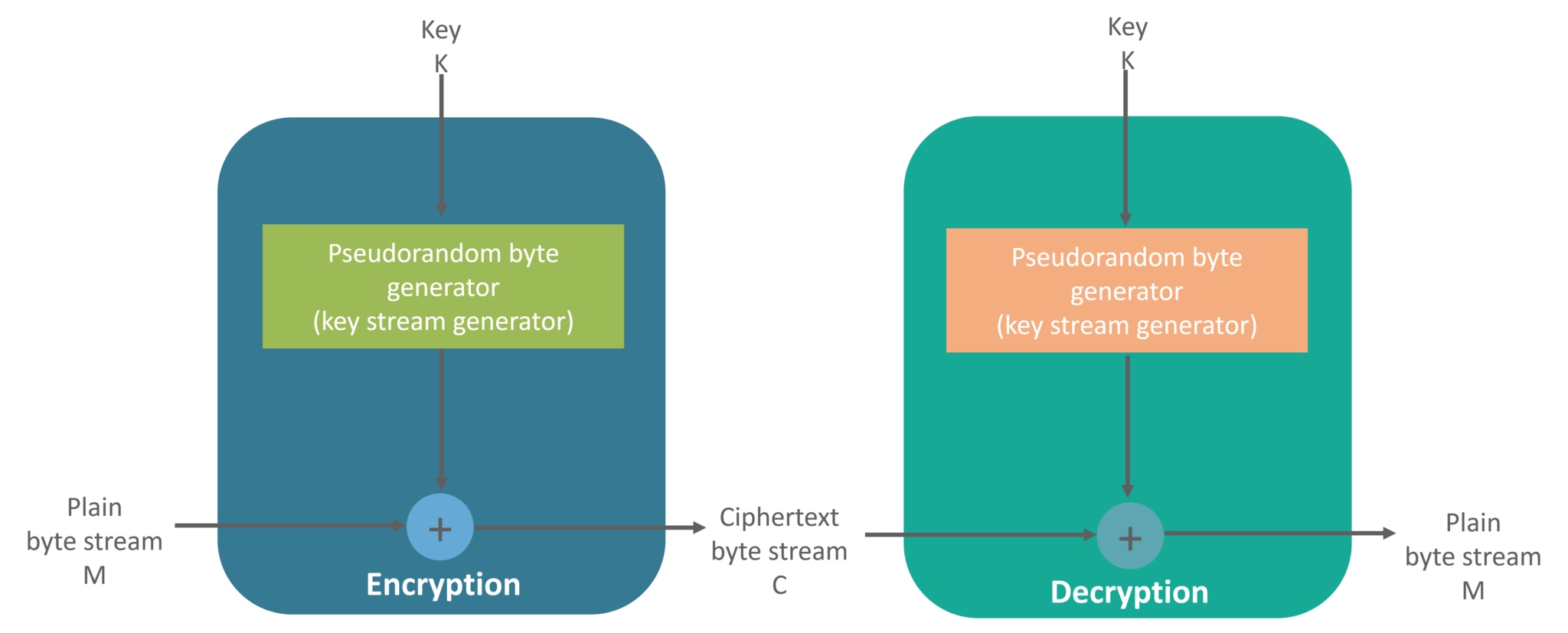
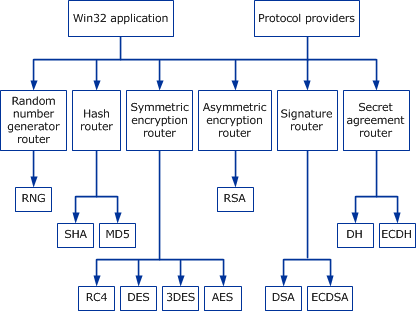
Pseudo-random permutation generators and cryptographic composition | Proceedings of the eighteenth annual ACM symposium on Theory of computing
Automated cryptocode generator is helping secure the web | MIT News | Massachusetts Institute of Technology
Example of key generation for code-based cryptography. The two matrixes... | Download Scientific Diagram

Distributing a Private Key Generator in Ad hoc Networks: Authority Distribution Using Threshold Cryptography: Stenberg, Eystein Måløy: 9783838387710: Amazon.com: Books

Build an Electronic Random Character Generator for One Time Pad Cryptography in Bamboo Case : 7 Steps (with Pictures) - Instructables