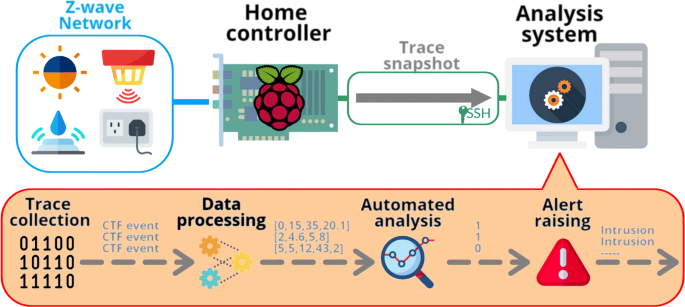
Multi-level host-based intrusion detection system for Internet of things | Journal of Cloud Computing | Full Text

Network intrusion detection system: A systematic study of machine learning and deep learning approaches - Ahmad - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

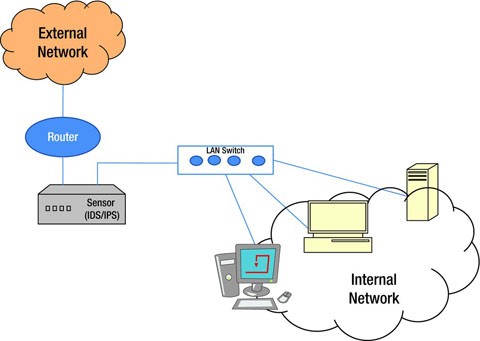
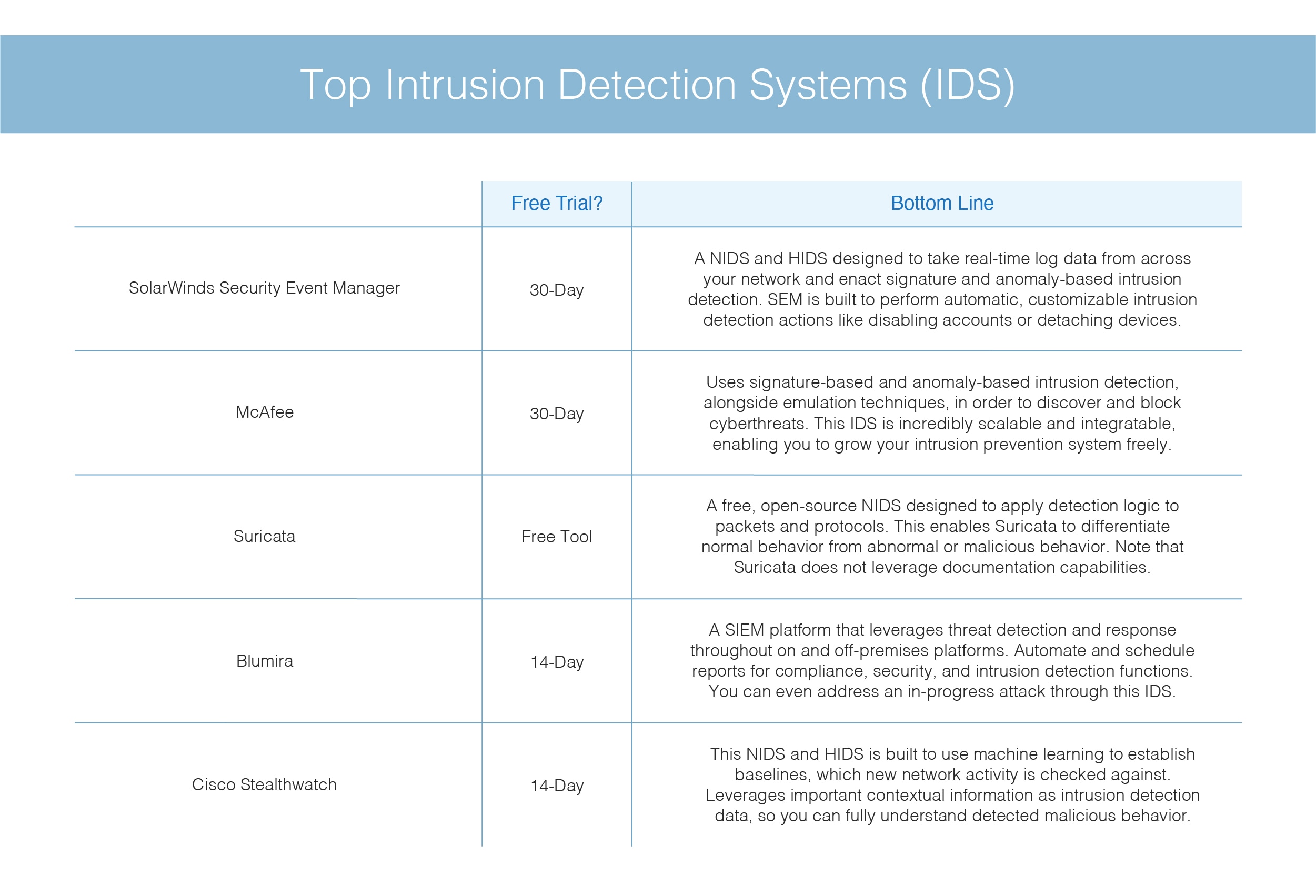
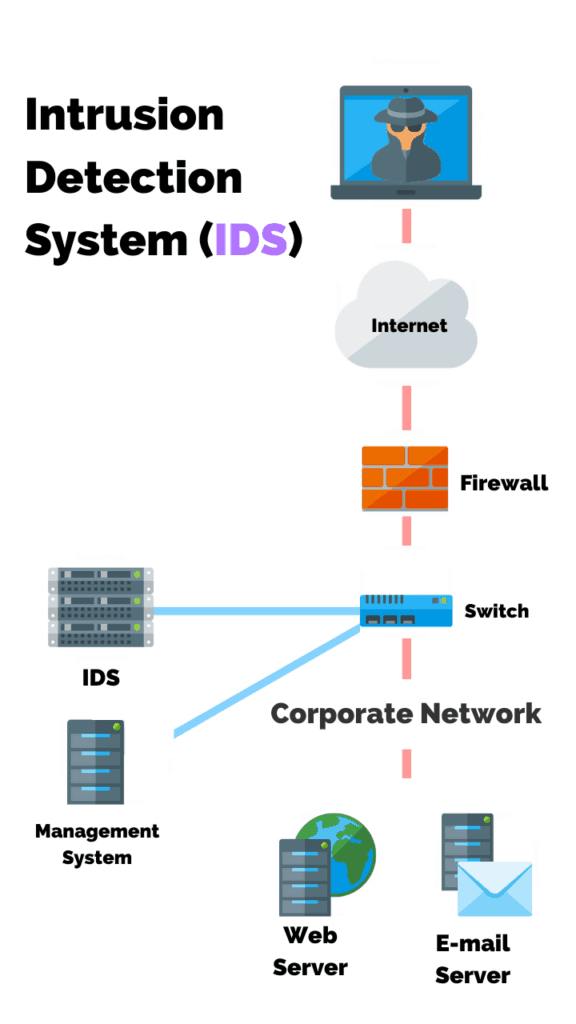
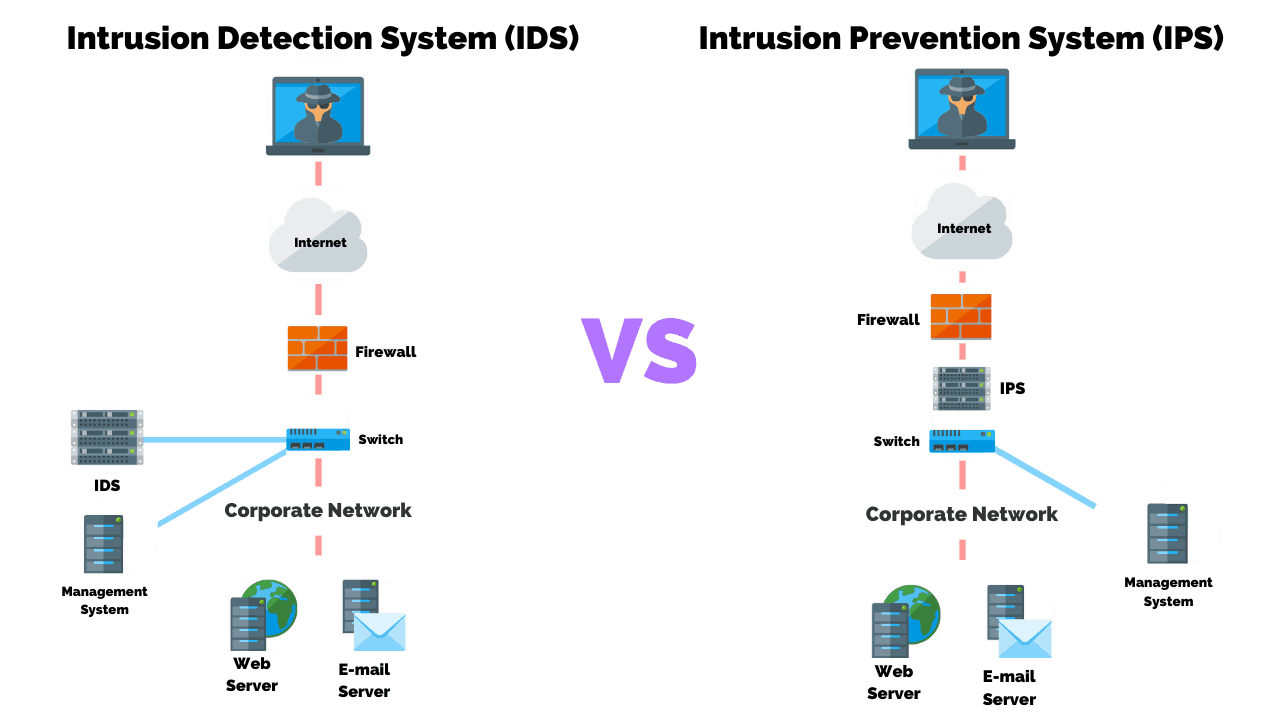
What Is Intrusion Detection and Prevention System? Definition, Examples, Techniques, and Best Practices | Spiceworks It Security

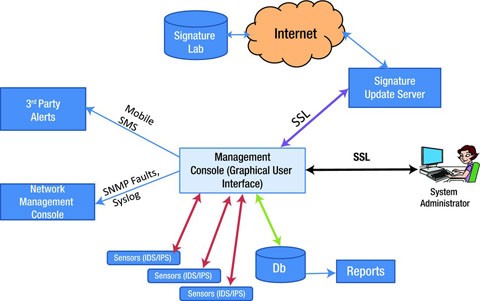
A survey on intrusion detection system: feature selection, model, performance measures, application perspective, challenges, and future research directions | SpringerLink

Differential early diagnosis of benign versus malignant lung cancer using systematic pathway flux analysis of peripheral blood leukocytes | Scientific Reports
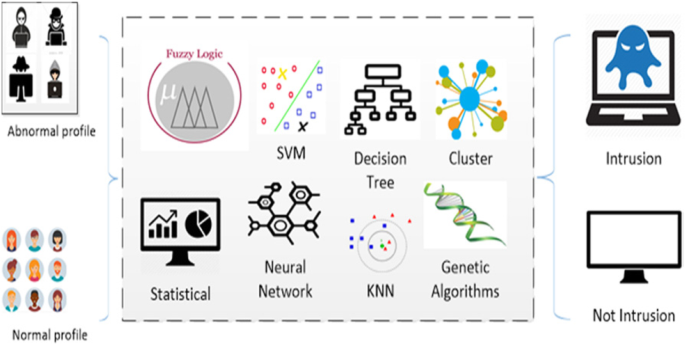
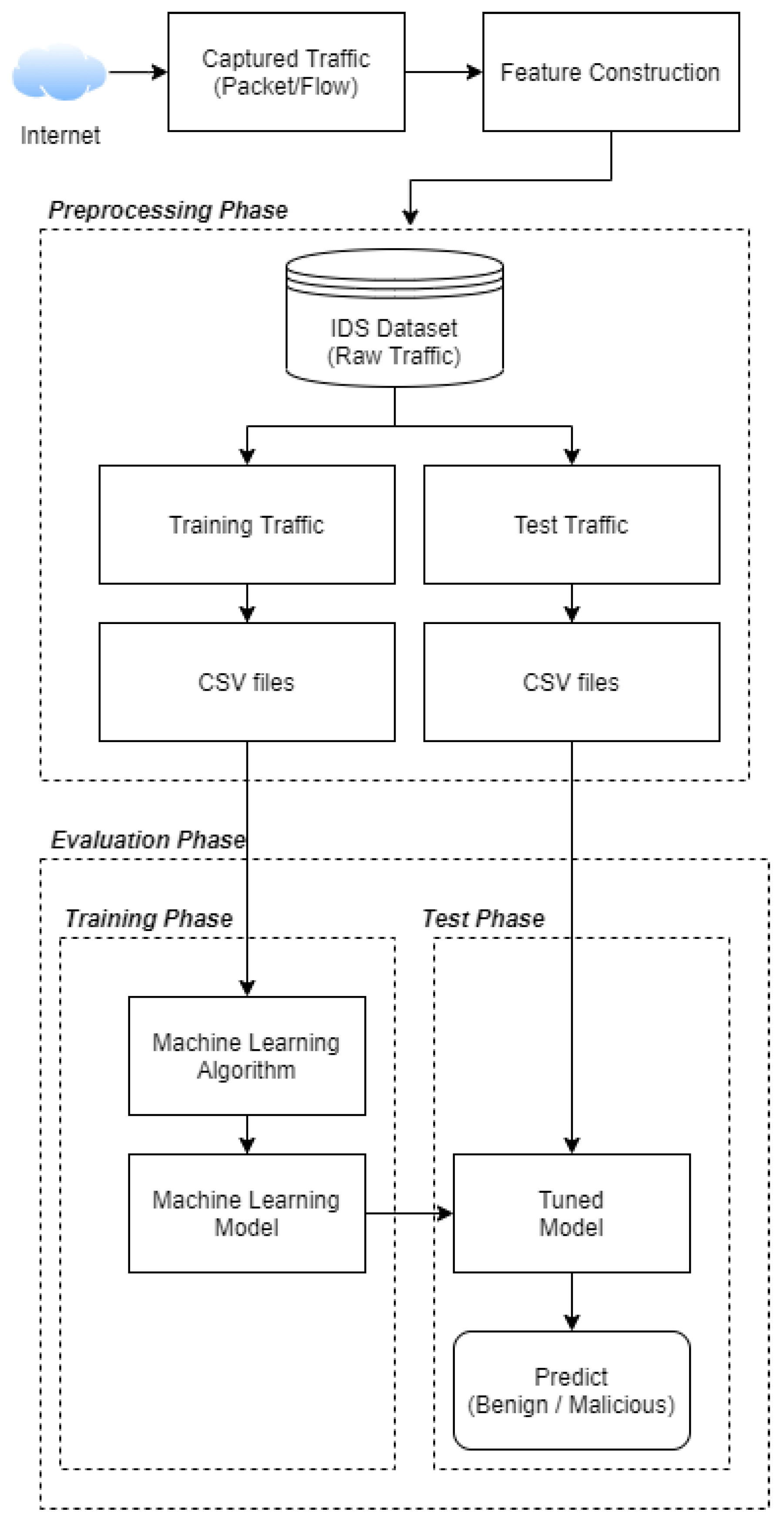
Survey of intrusion detection systems: techniques, datasets and challenges | Cybersecurity | Full Text


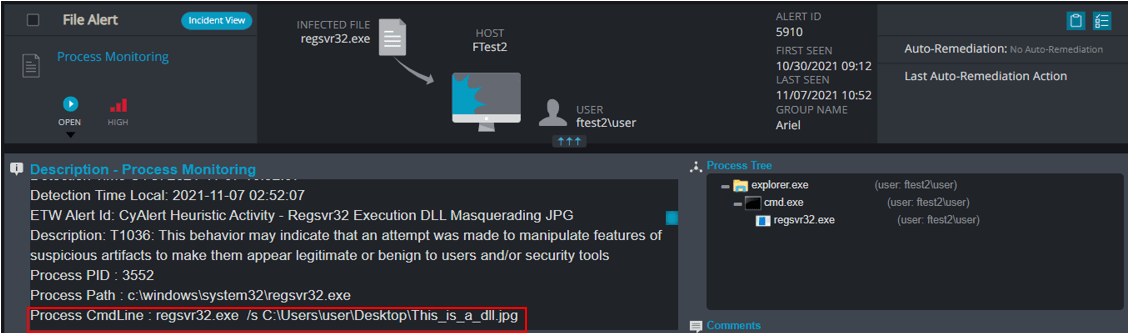
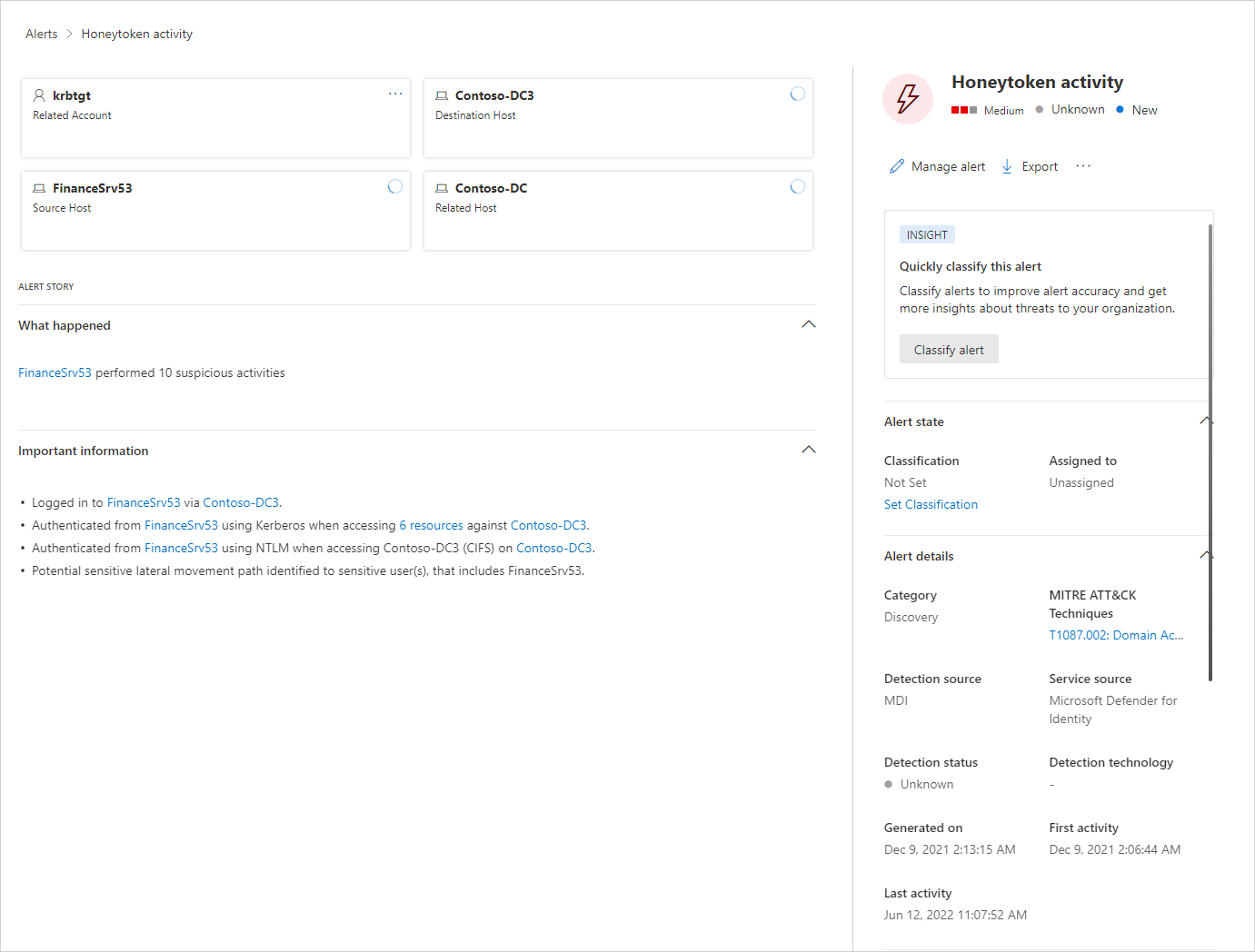
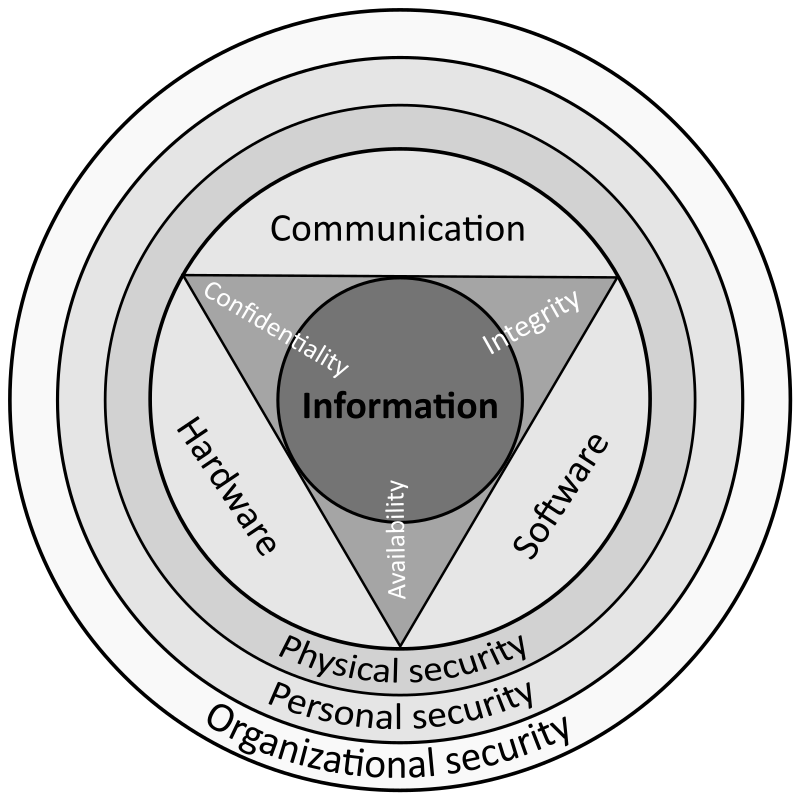

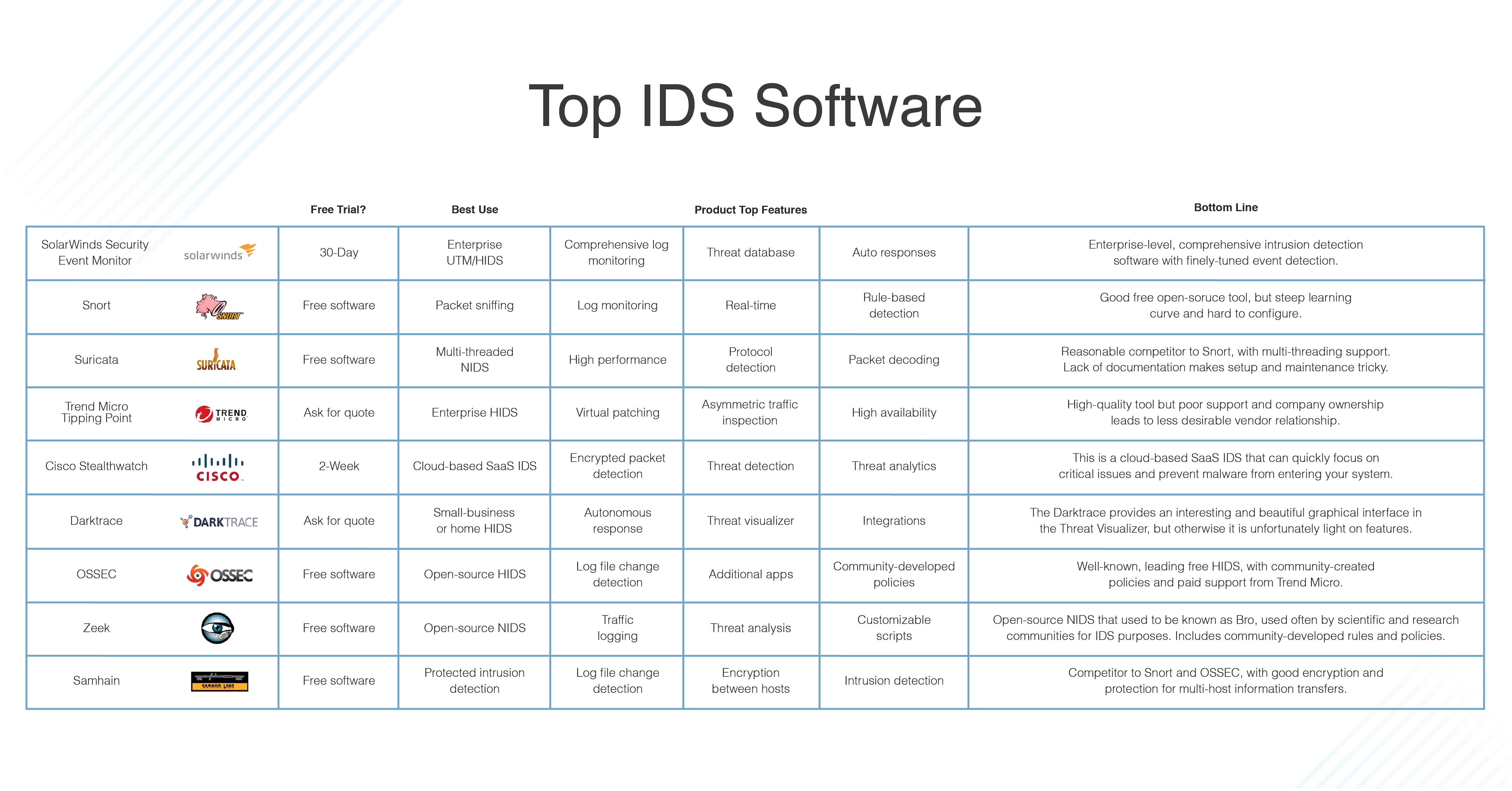
![Detections and alerts | Elastic Security Solution [8.5] | Elastic Detections and alerts | Elastic Security Solution [8.5] | Elastic](https://www.elastic.co/guide/en/security/current/images/alert-page.png)