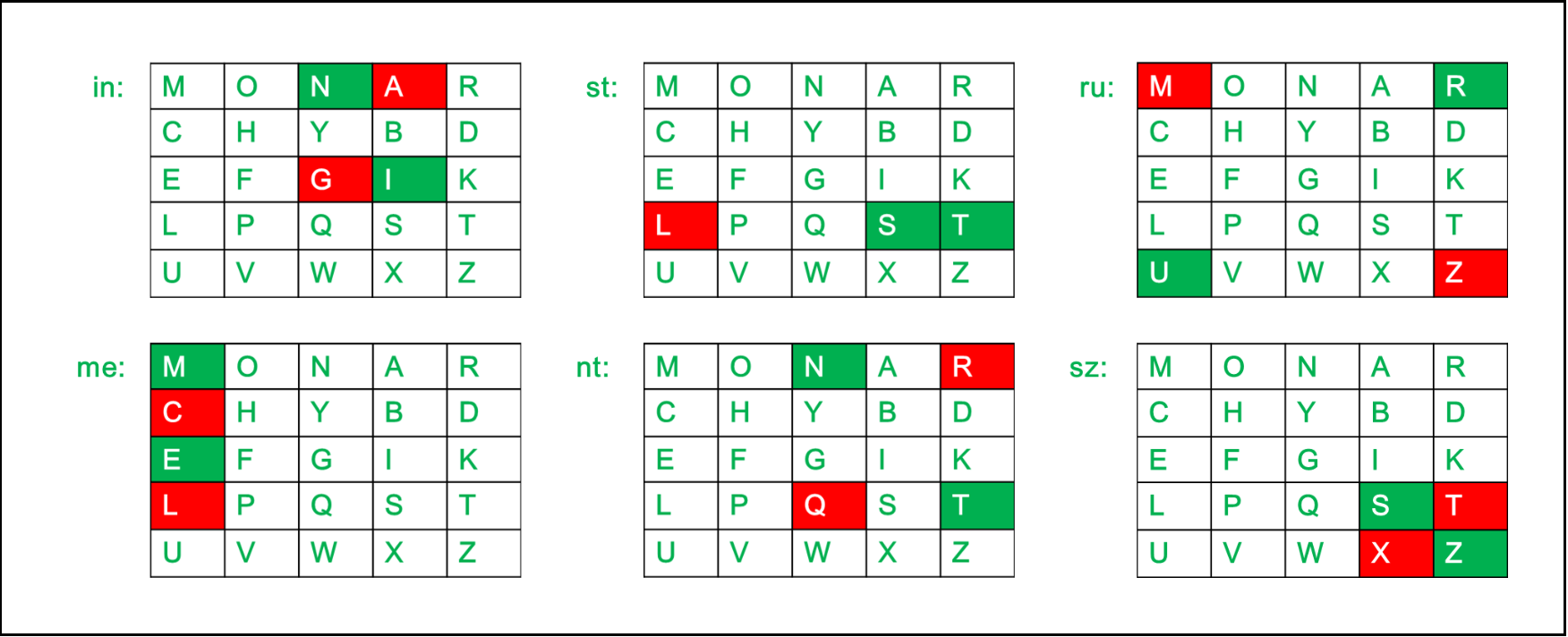
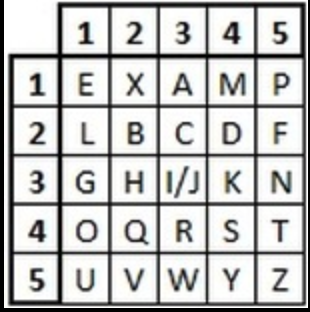
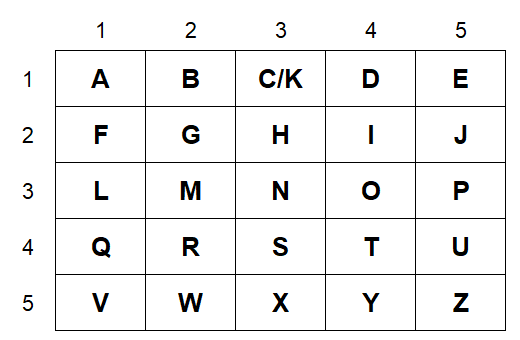
What is the rule for encryption in the Playfair cipher if the letters in a pair do not appear in the same row or column? - Quora

CIT 380: Securing Computer SystemsSlide #1 CIT 380: Securing Computer Systems Classical Cryptography. - ppt download

Table 5 from Improvement of 16 X 16 Playfair Cipher using Random Number Generator | Semantic Scholar