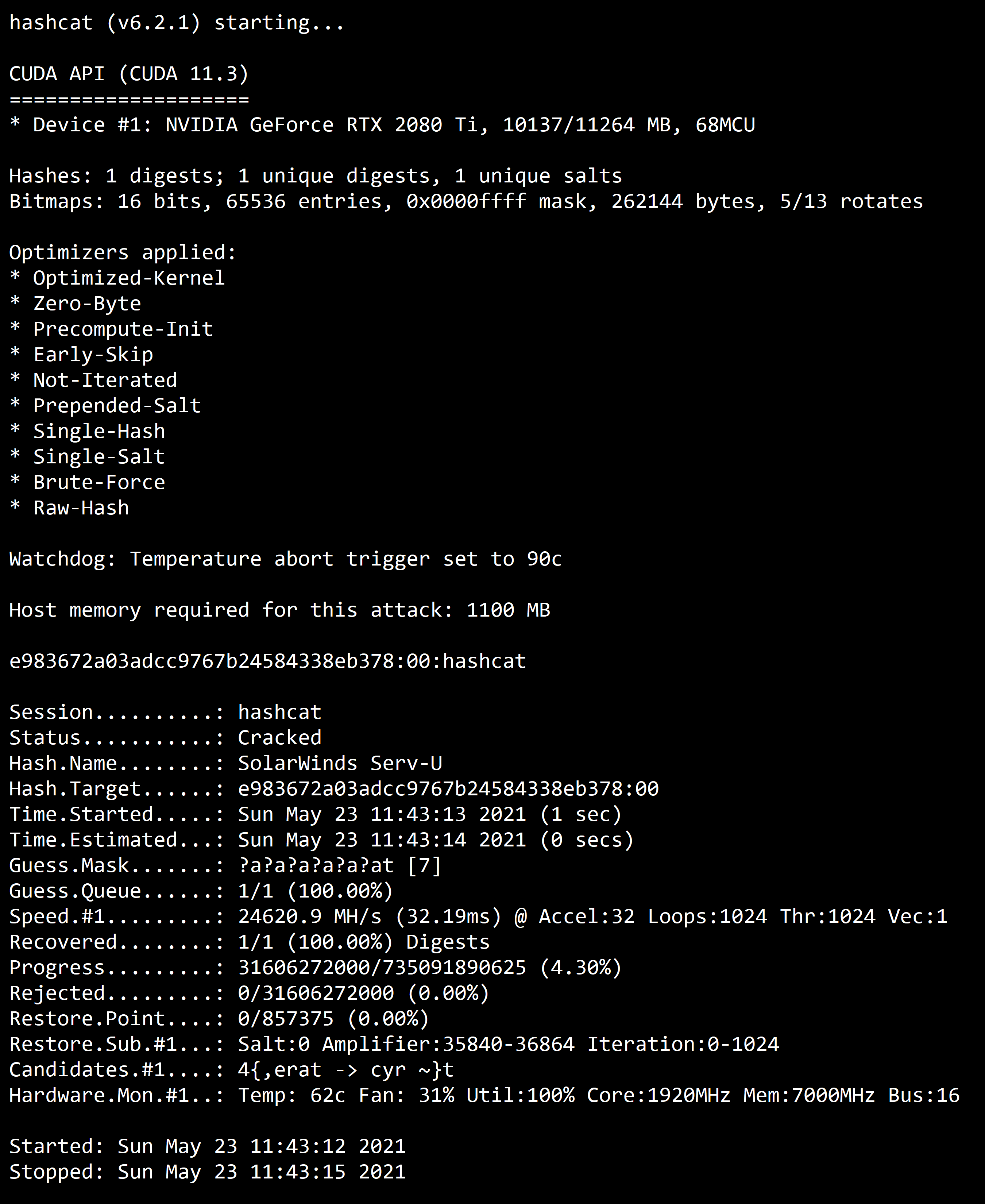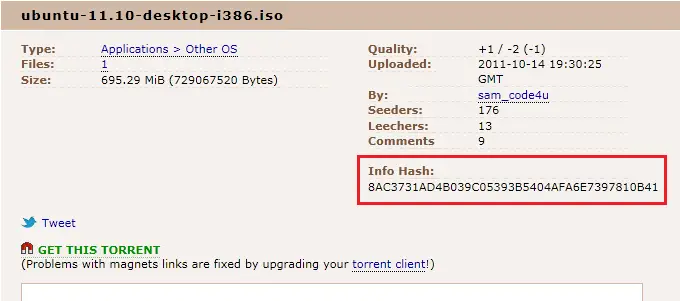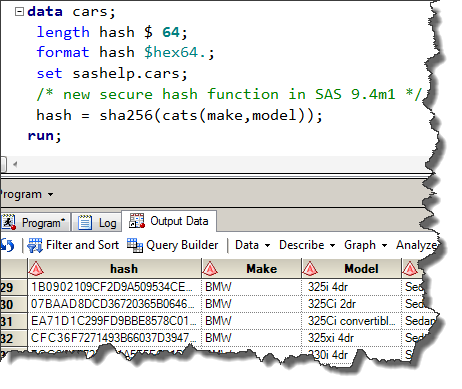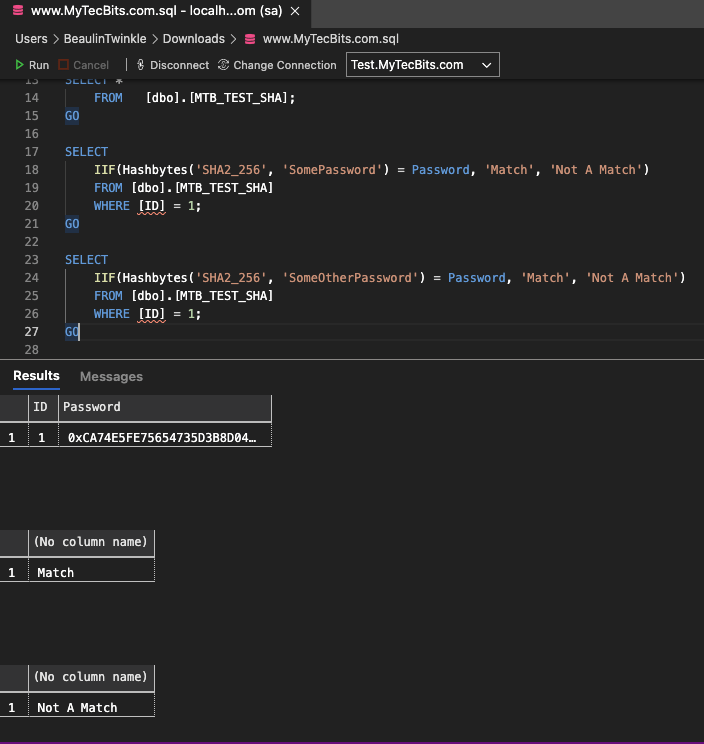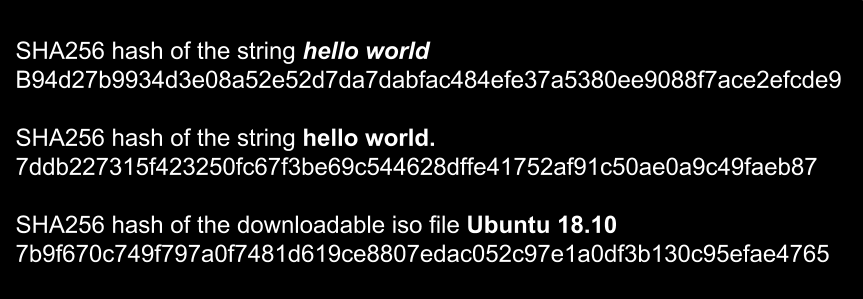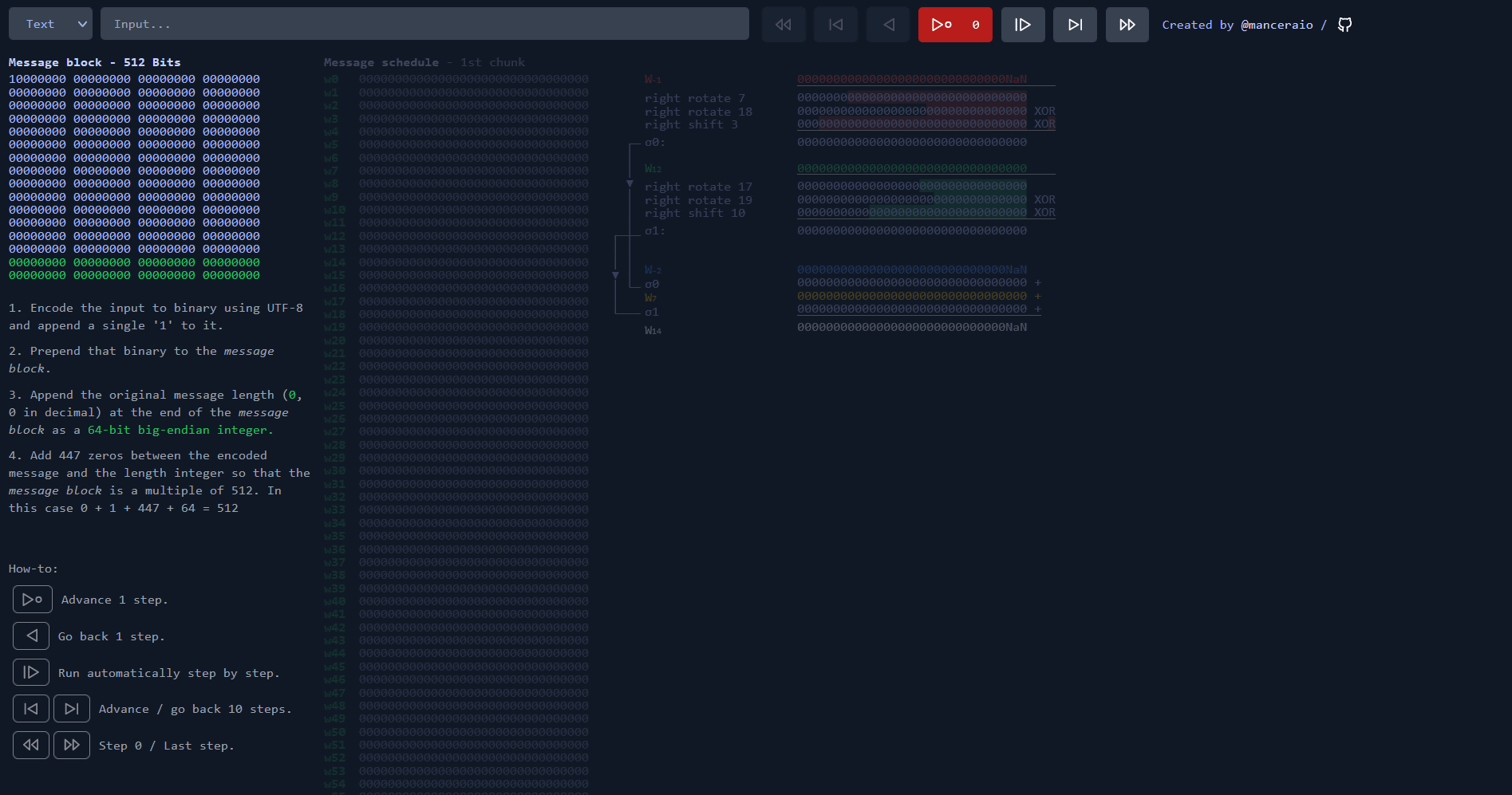
Sha256 Algorithm Explained' that visualizes the calculation process of the hash function 'SHA-256' in an easy-to-understand manner - GIGAZINE
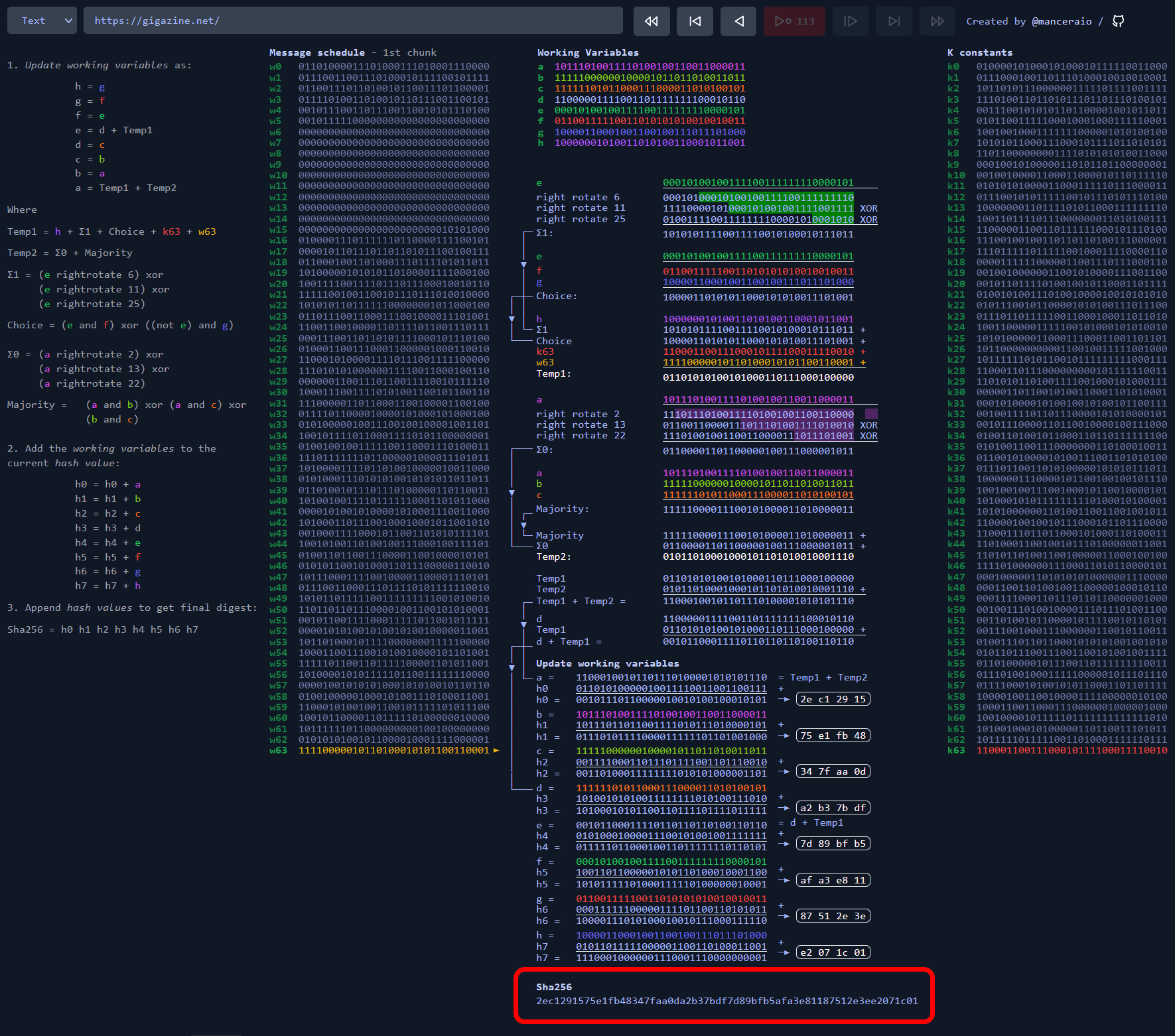
Sha256 Algorithm Explained' that visualizes the calculation process of the hash function 'SHA-256' in an easy-to-understand manner - GIGAZINE
QR-code example: generating SHA1 and SHA-256 base64 encoded checksum issue. · Issue #49 · googlesamples/android-testdpc · GitHub
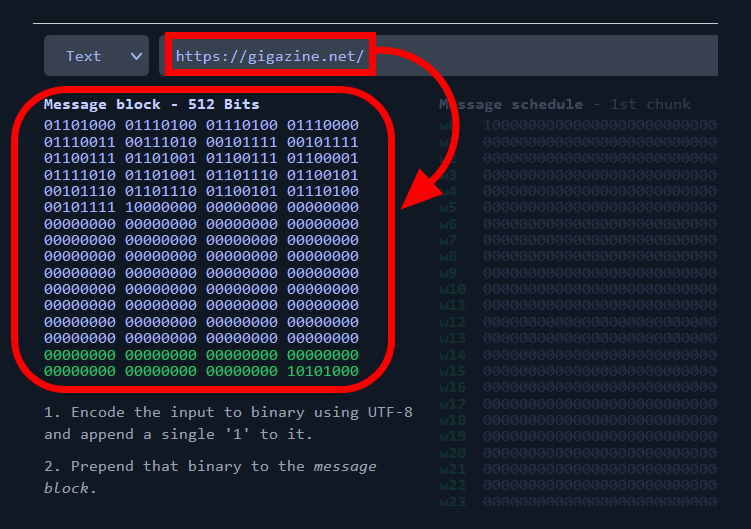




![Free] Checksum Generator - General - Xojo Programming Forum Free] Checksum Generator - General - Xojo Programming Forum](https://forum.xojo.com/uploads/default/optimized/2X/a/a3989206344d4b7beebaba643d89e09d8475eb65_2_1024x488.png)