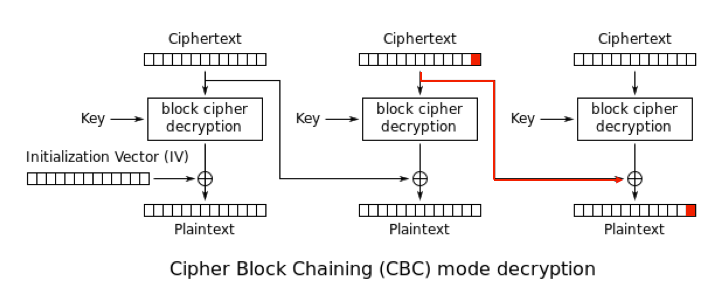
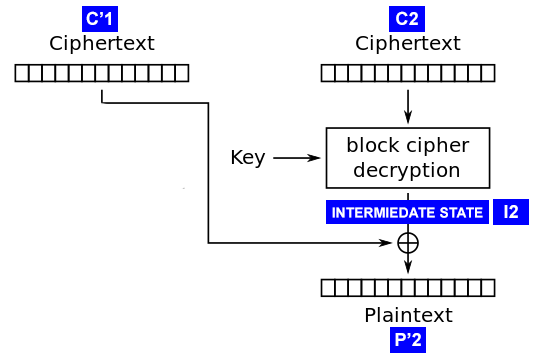
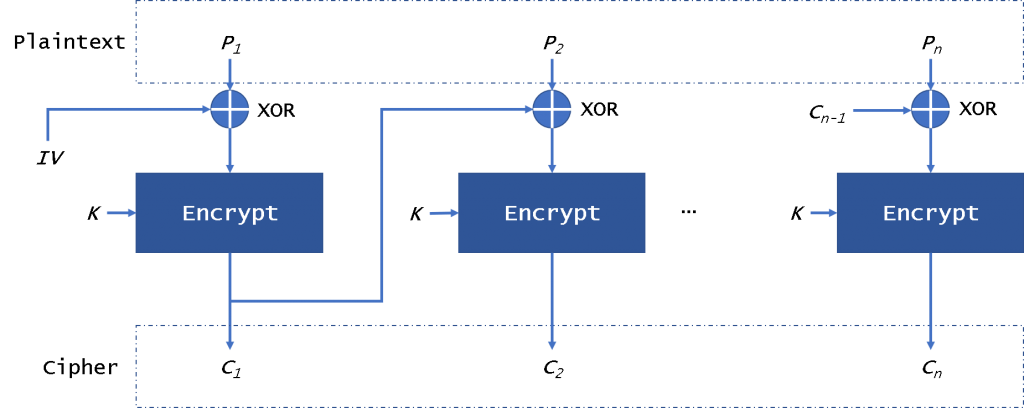
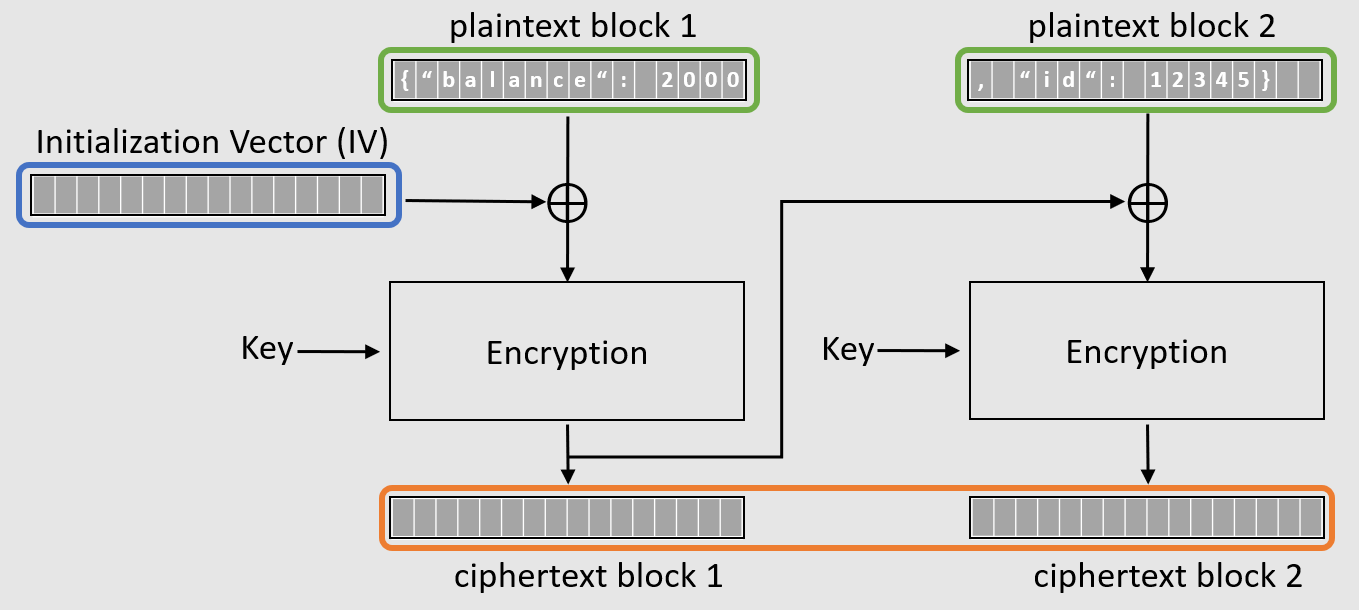
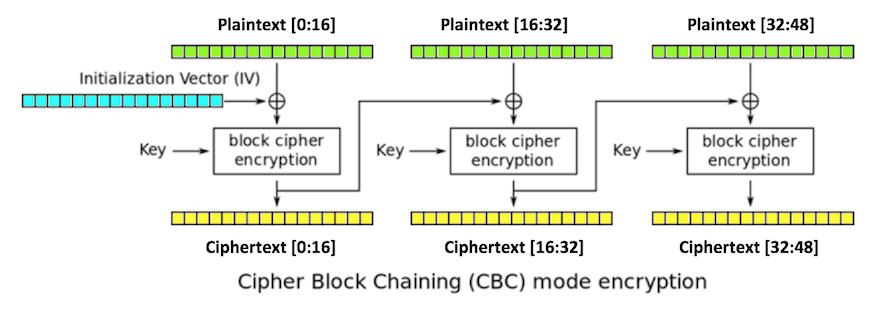
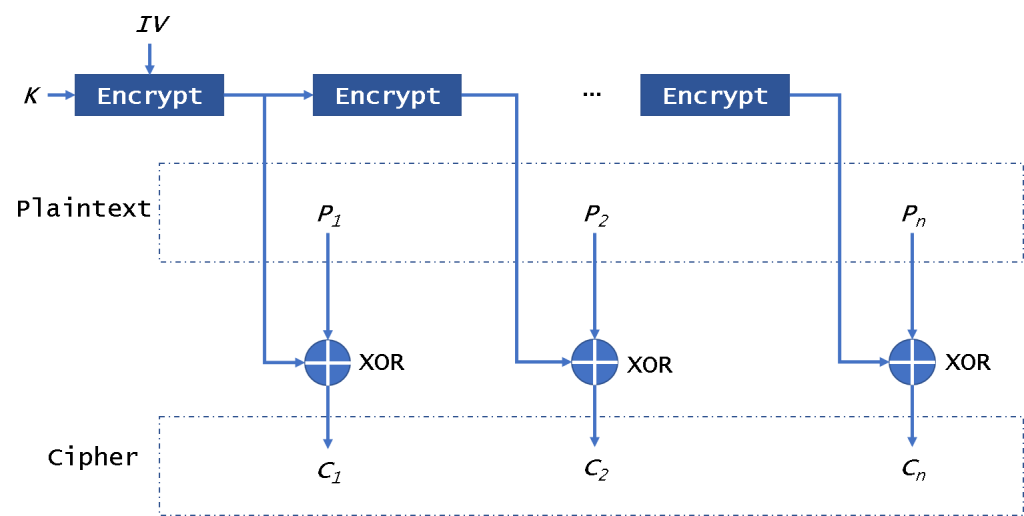
aes - CMAC Generation : If input payload length is not aligned in 16 bytes, what are the possible side effects? - Cryptography Stack Exchange
Security Best Practices: Symmetric Encryption with AES in Java and Android | by Patrick Favre-Bulle | ProAndroidDev
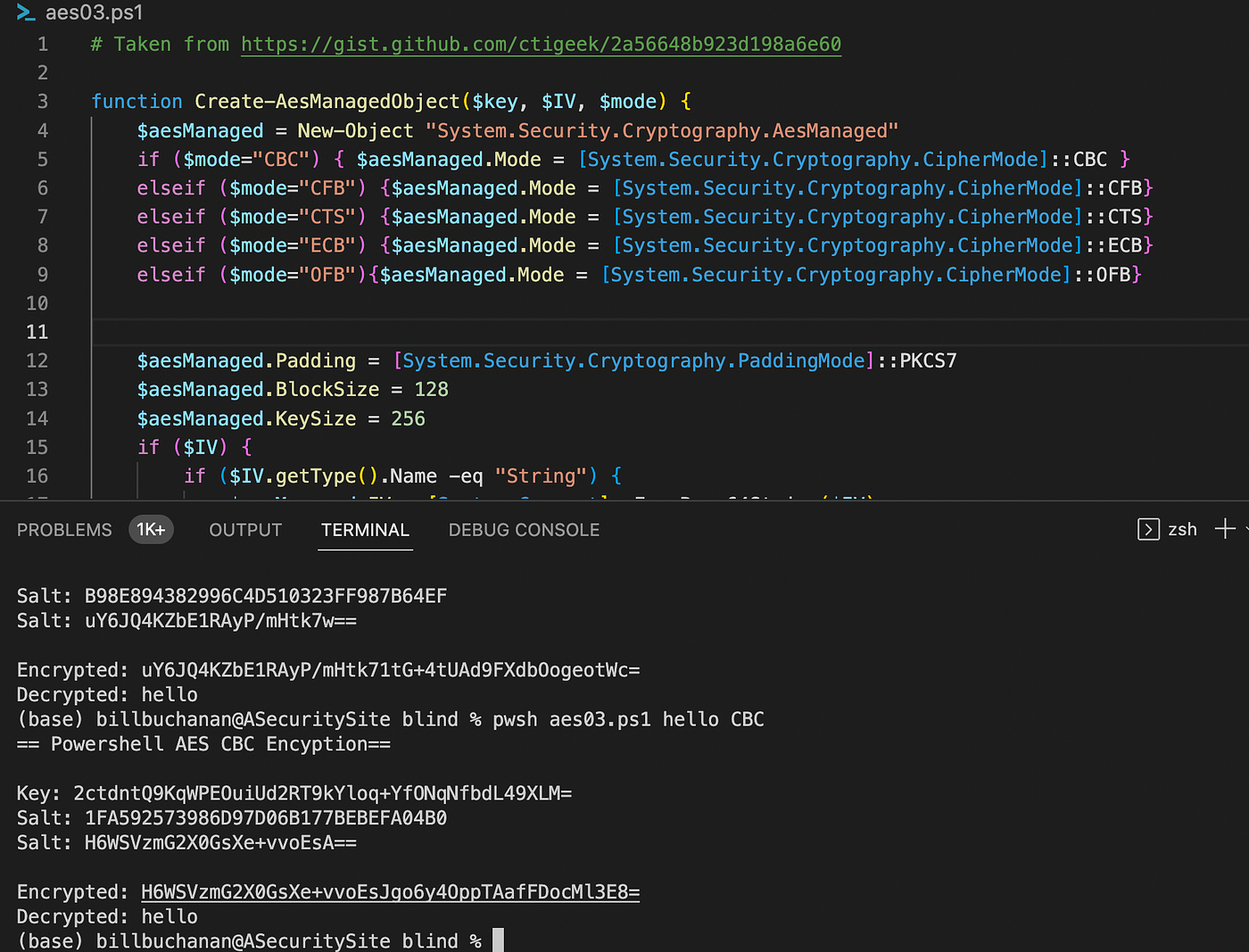
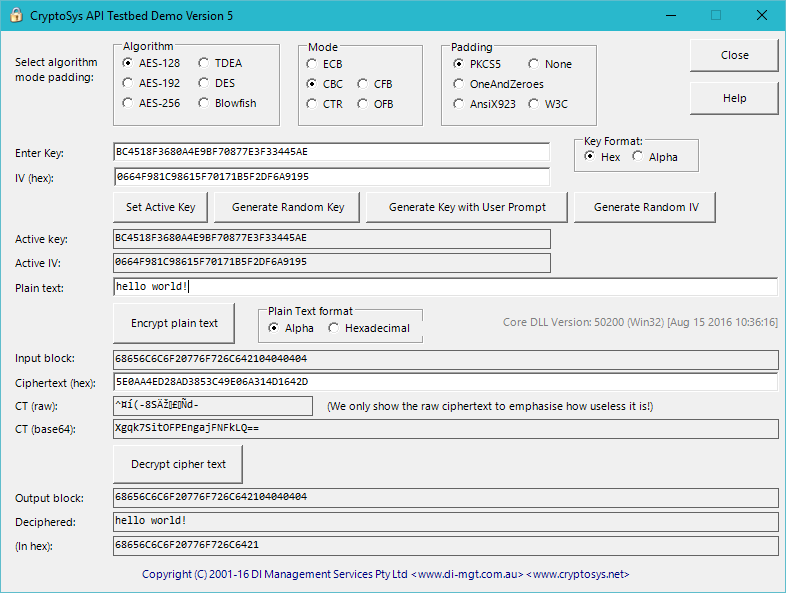
AES Encryption With PowerShell. Powershell isn't just for Windows, it… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium